
CertiK Skynet Quest Answer (Security Analysis)
CertiK Skynetクエストの答えです。
当サイトに含まれる情報もしくは内容を利用することに伴い直接・間接的に生じた損失等に対し、当方は一切の責任を負いません。
ご自身の判断でご利用ください。
Security Analysis
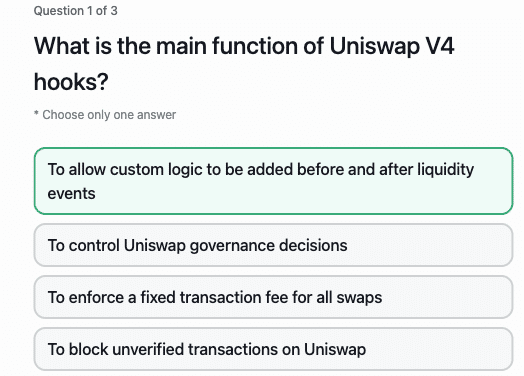
Understanding Uniswap V4 Hooks and Their Security Implications


CertiK Hack3d 2024 Part 1 - Web3 Security by the Numbers



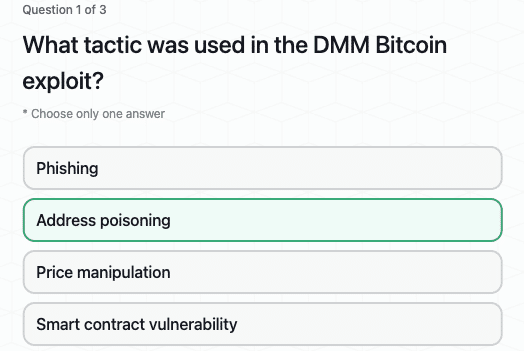
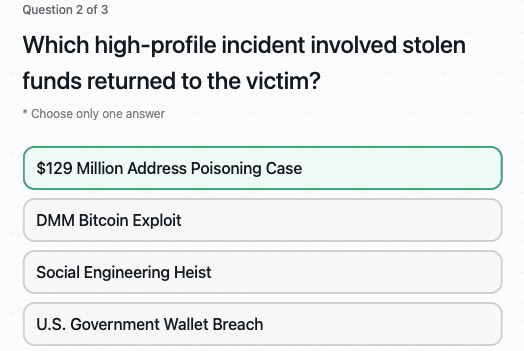
CertiK Hack3d 2024 Part 2 - Uncovering Major Incidents

CertiK Hack3d 2024 Part 3 - Building a Resilient Web3 Ecosystem


Case Study on the Risks of Phishing Attacks in DeFi



Sonne Finance Incident Analysis


Enhancing Security Awareness for Web3 Desktop Wallets
CryptoBottle Incident Analysis
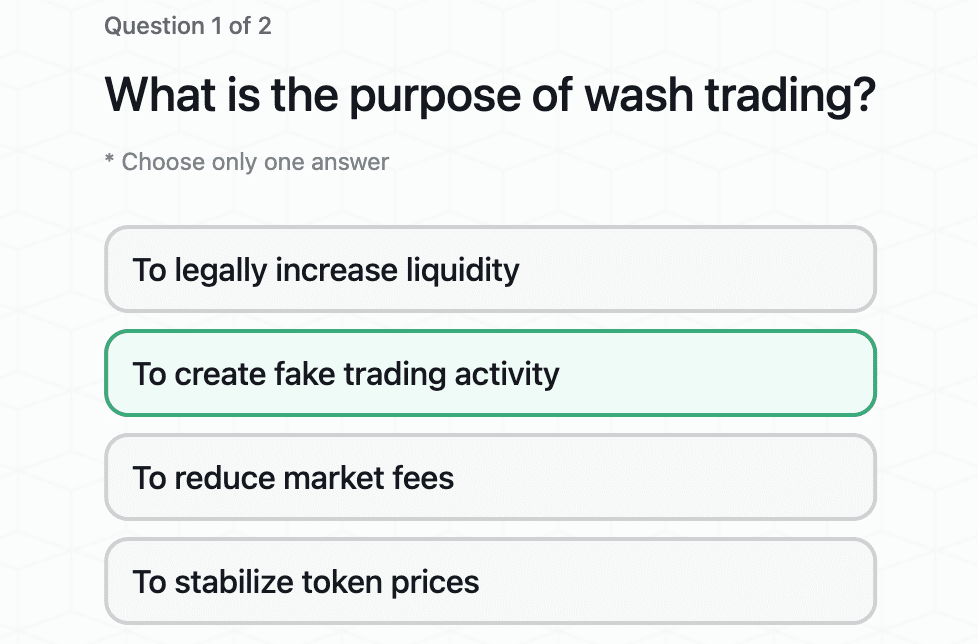
Identifying Crypto Market Manipulation

Defending Against Clipper Malware



Clipper DEX Withdrawal Vulnerability Exploit



The Memecoin Markets of Springfield



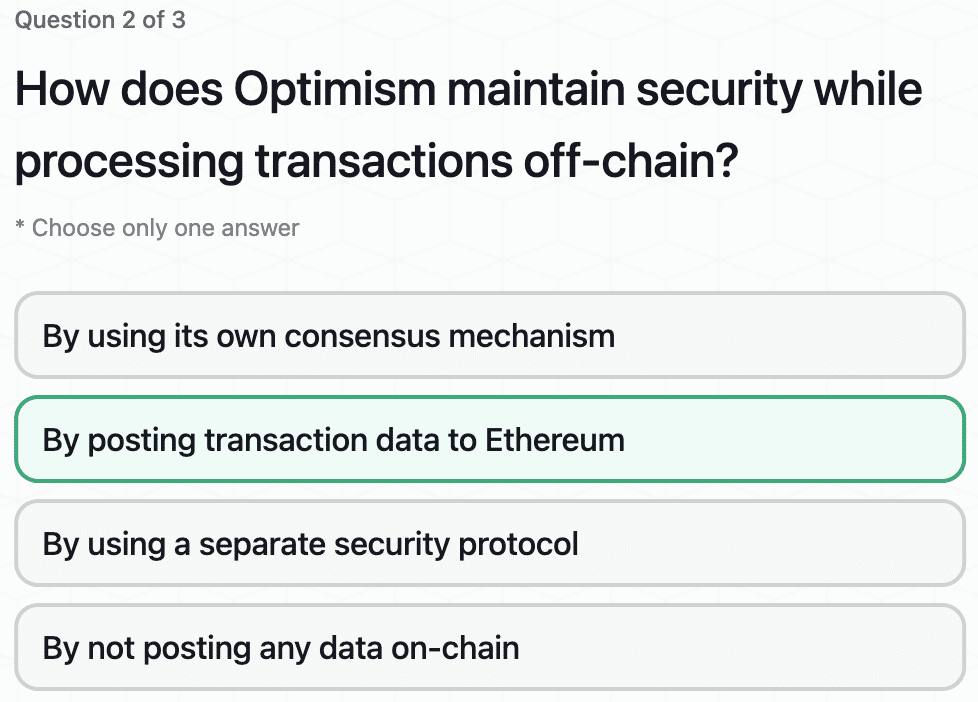
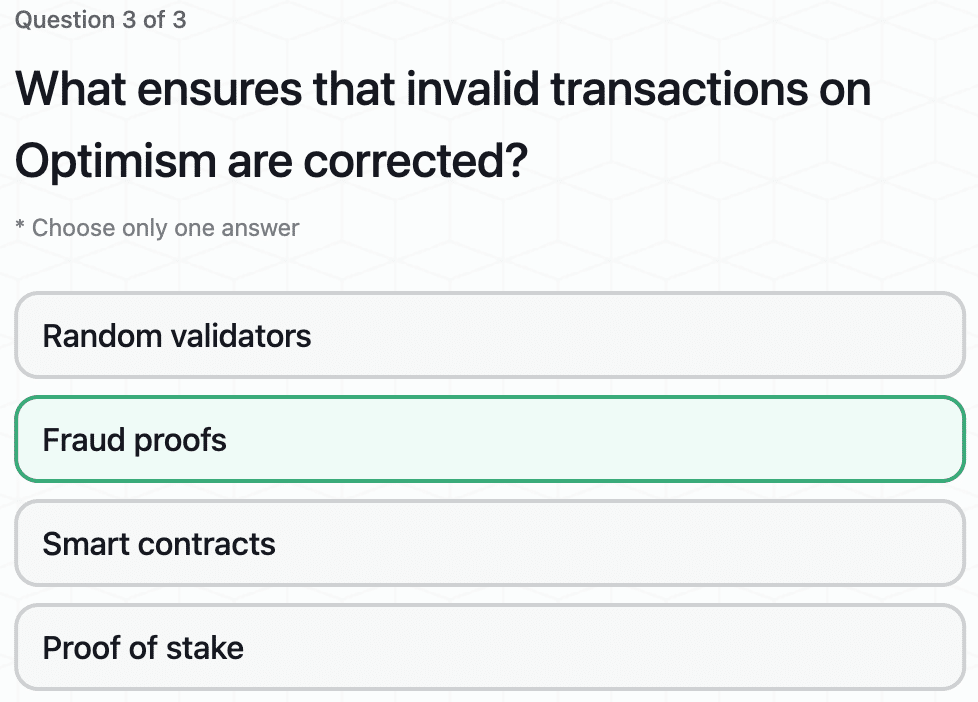
Exploring the Security Model for Optimism’s Superchain

Navigating DAO Governance and the Compound DAO Incident



Understanding the Polter Finance Exploit



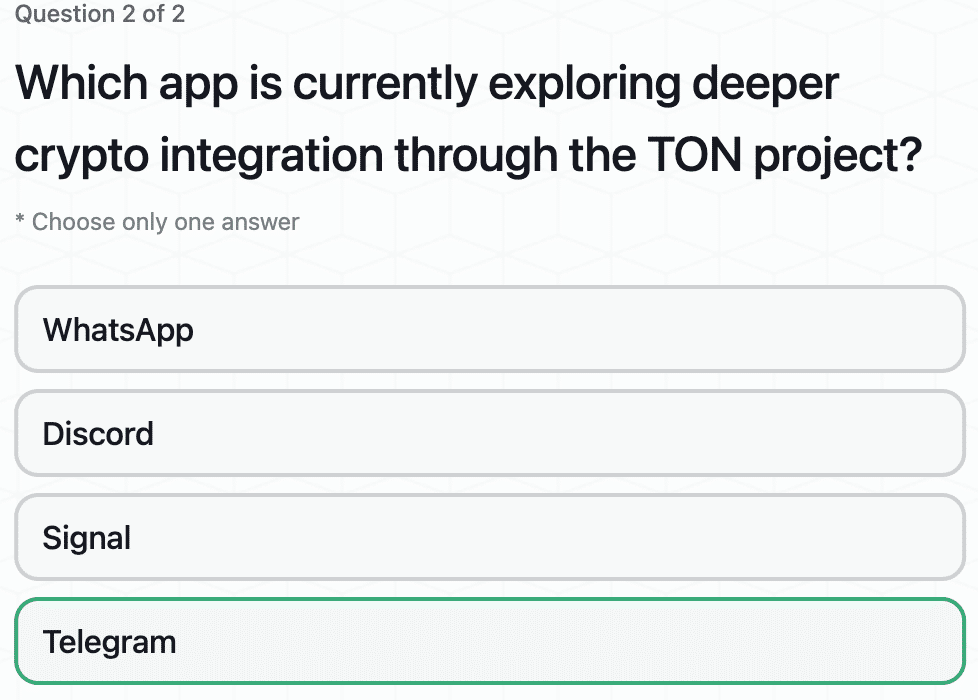
Evaluating Popular Web3 Messaging Apps





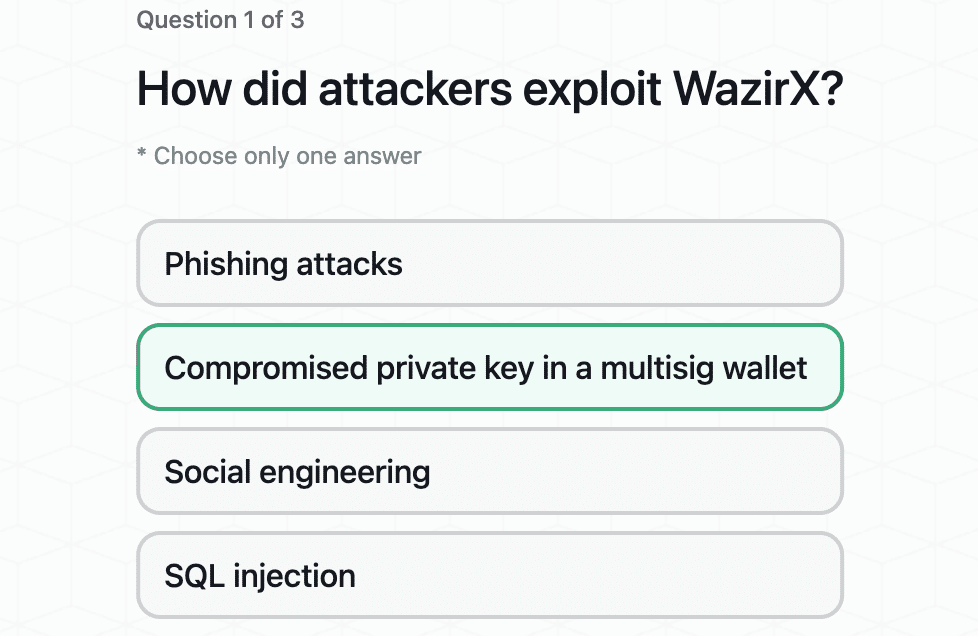


UtopiaSphere Incident Analysis


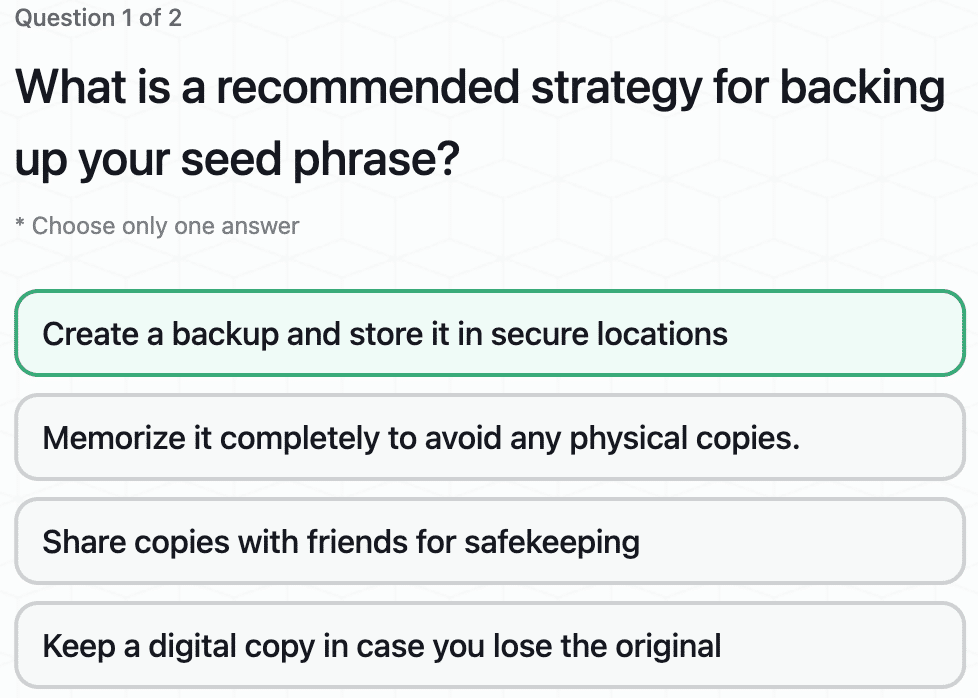
Private Key Security: Seed Phrases



HACK3D Part 3: Rounding Issue Exploits



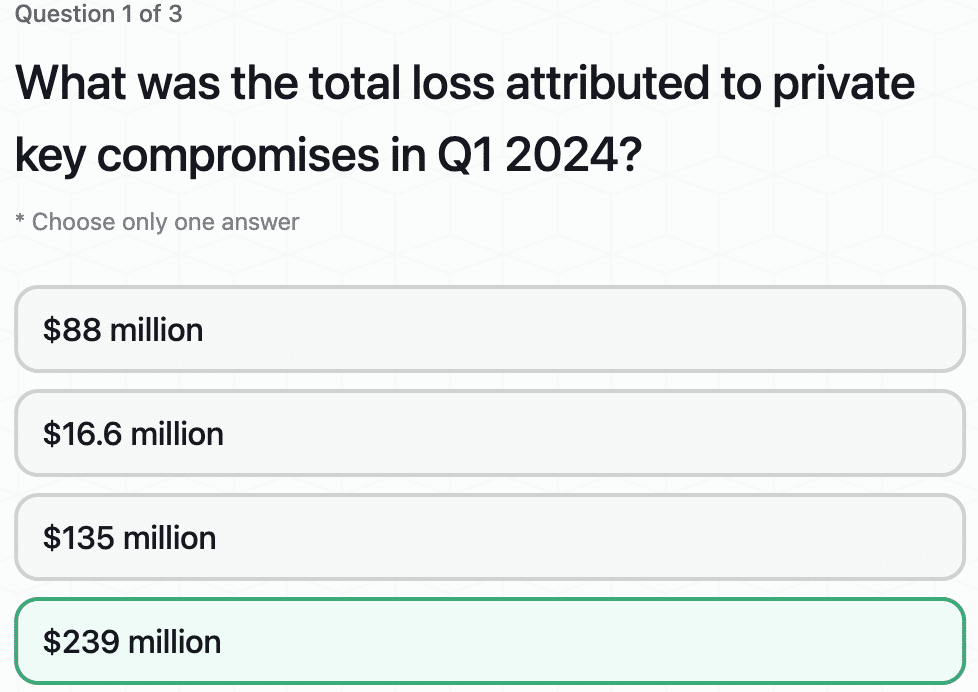
HACK3D Part 2: Private Key Compromise


HACK3D Part 1: Top Incident Analyses



Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan - Part 2



Analyzing Security for Solana-Based Memecoins with CertiK’s Token Scan - Part 1



