
CertiK Skynet Quest Answer (Web3 Fundamentals)
CertiK Skynetクエストの答えです。
当サイトに含まれる情報もしくは内容を利用することに伴い直接・間接的に生じた損失等に対し、当方は一切の責任を負いません。
ご自身の判断でご利用ください。
Web3 Fundamentals
Exploring PSBT in Bitcoin DeFi Ecosystem



Fundraising in the Web3 Industry




Stablecoin Risks: Identifying and Mitigating Vulnerabilities




Understanding Stablecoin Reserves








Understanding U.S. Crypto Tax Forms



Exploring the Rise of AI Memecoins






Proof of Work versus Proof of Stake










Importance of Bug Bounty Programs in Web3



Hackers Infiltrating Crypto Job Boards



Understanding Soft Rug vs. Hard Rug Pulls


Protecting Your PostgreSQL Database from Cryptojacking



Understanding Economic Exploits and Tokenomics






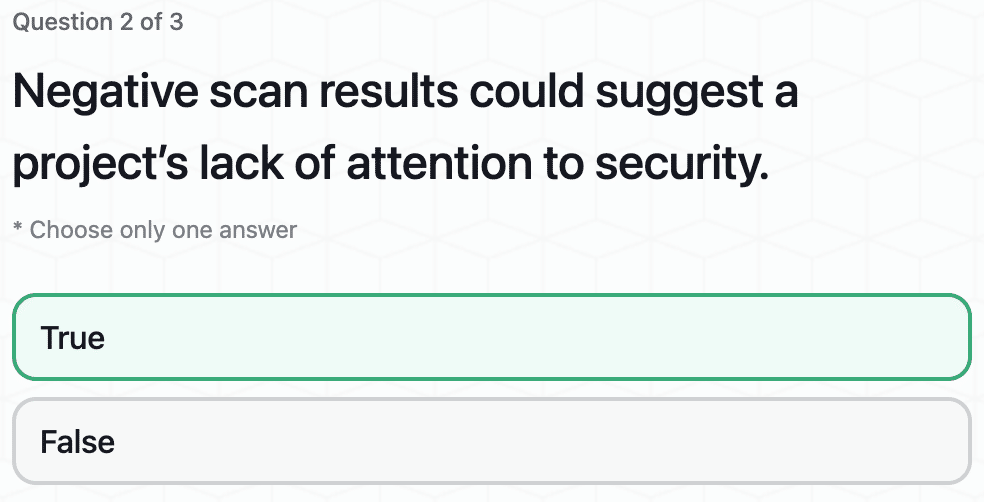
Operational Security via Website Scan


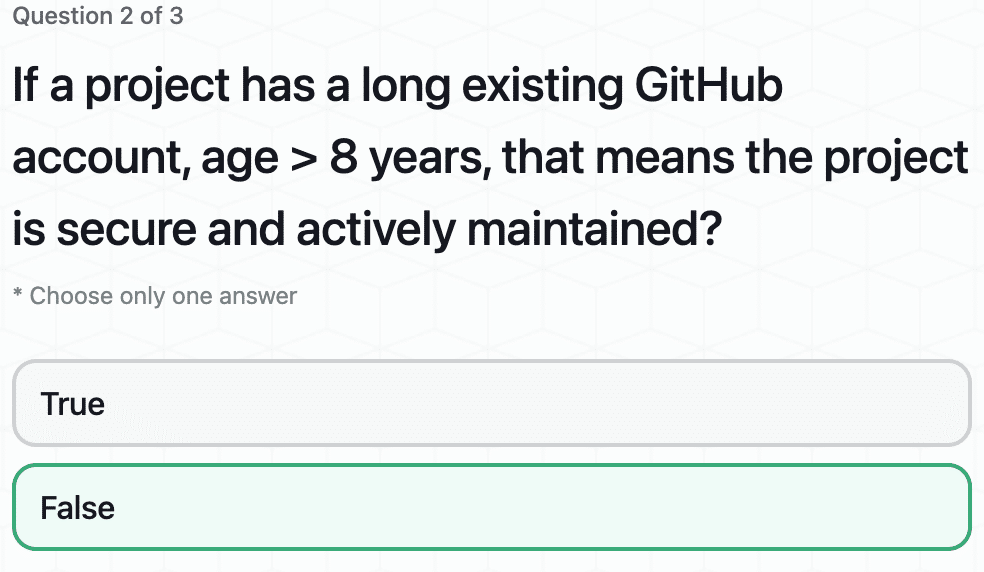
GitHub Monitoring for Better Code Security


Governance Activity Monitoring



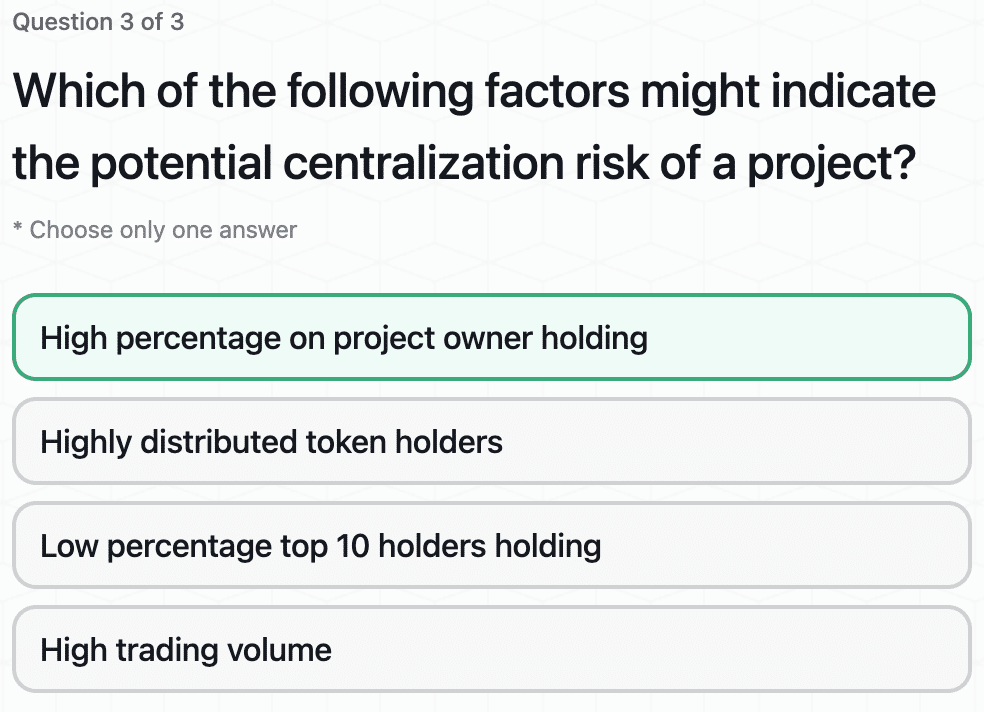
Insights on Token Holder Analysis


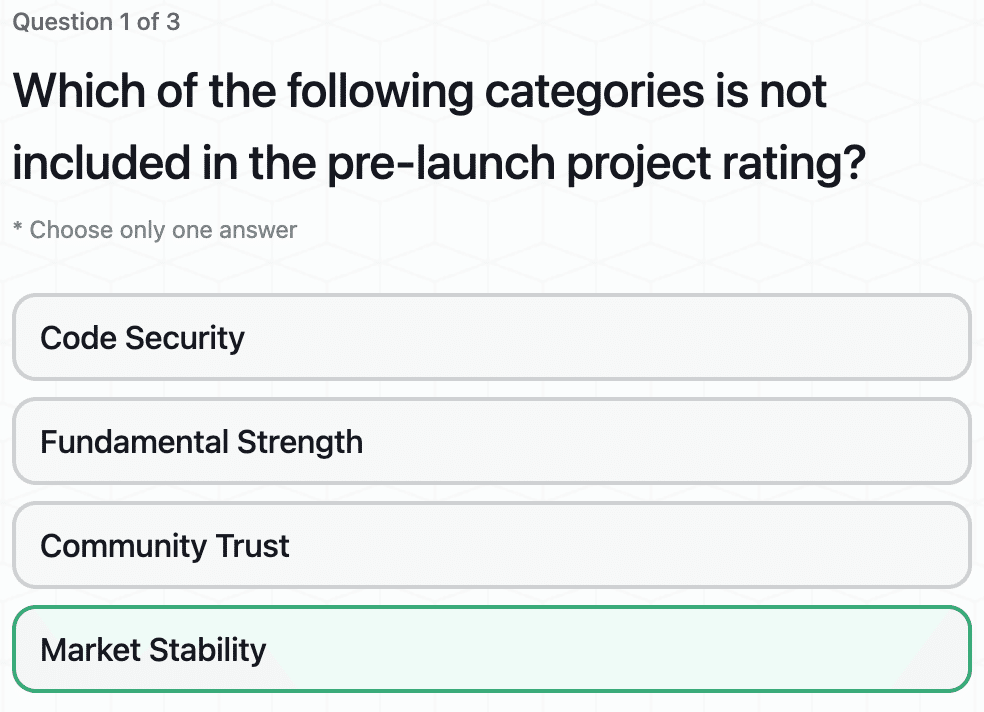
Security Rating for Pre-Launch Projects

Navigating NFT Security and Avoiding Scams



Protecting Against Social Engineering Attacks






Setting Up a Security War Room



Understanding and Mitigating 51% Attacks


Multi-Signature Wallets Explained
Question 1 of 3 : To require multiple approvals for transactions
Question 2 of 3 : 3
Question 3 of 3 : False
SOC 2 Compliance for Crypto Companies



Case Study on Enhancing Security for App Chains


DEXTools | Real-Time Trading Insights




Intro to AML and its Role in Crypto






Understanding Chain Hopping and Crypto Money Laundering

How the DHS is Stopping Ransomware Attacks



Introduction to Account Abstraction


Empowering Your Web3 Journey with Advanced Security Tools



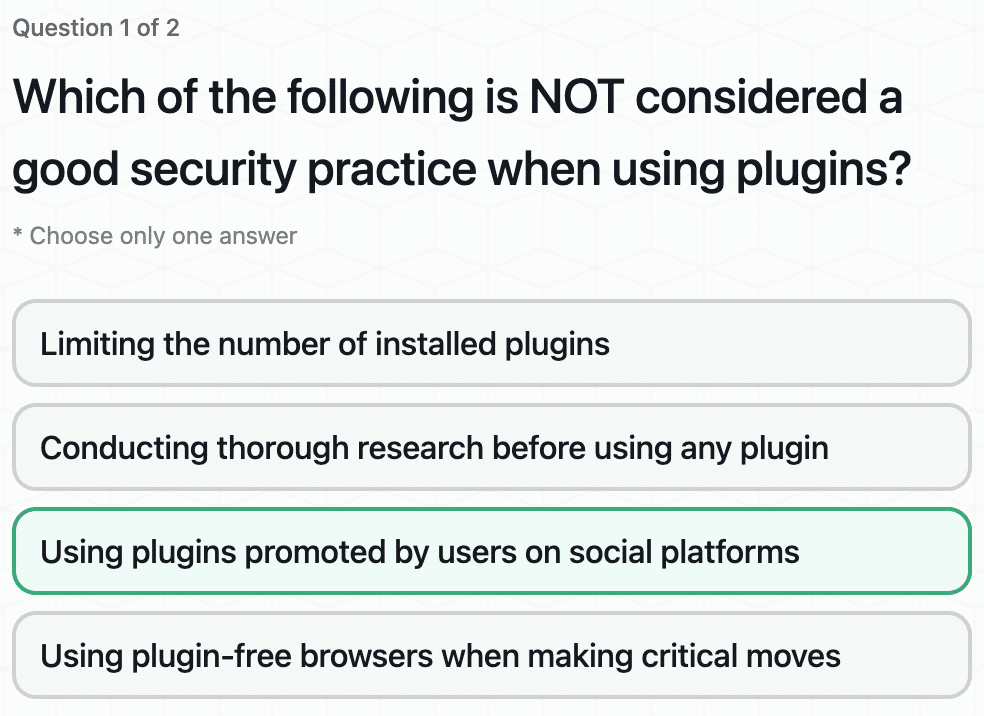
Stay Vigilant on Browser Plugins

Evaluating Cryptocurrency News Sources



Understanding and Preventing Sybil Attacks



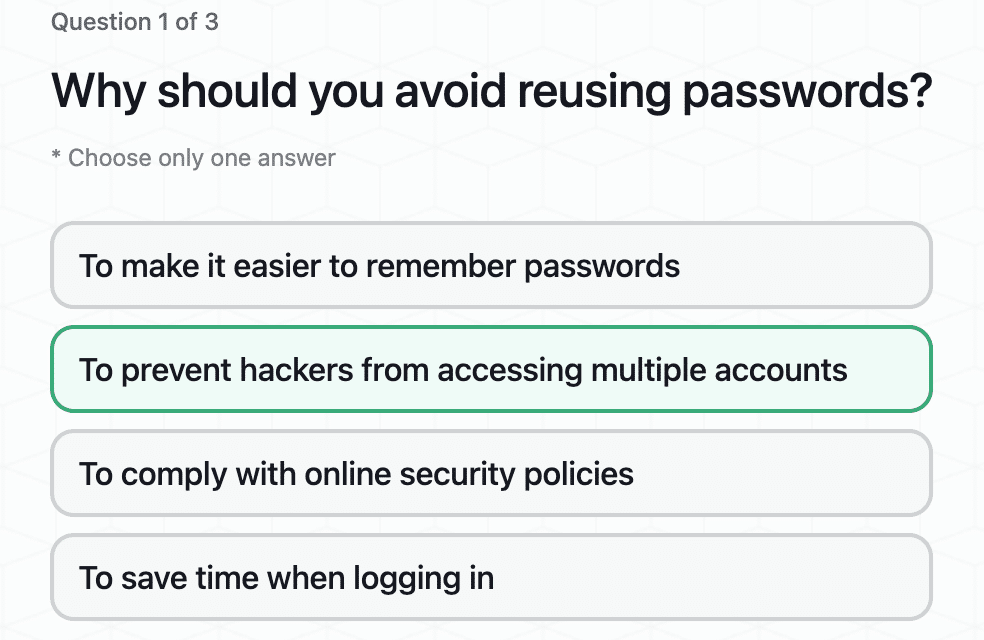
How to Create and Maintain Secure Passwords


Top Compliance Risks in Crypto



Introduction of Diamond Agency Contract



Best Practices for Wallet Security

Losses Related to Private Key Compromises

Identifying Malicious Activity on Websites & dApps


Introduction to Formal Verification


Understanding the Peel Chain Technique


Identifying and Avoiding Phishing Scams in X Replies





Protecting Yourself from Discord Scams

Different Mechanisms for Honeypot Scams



Governance and Security in DAOs




Community and Security Risks in Web3
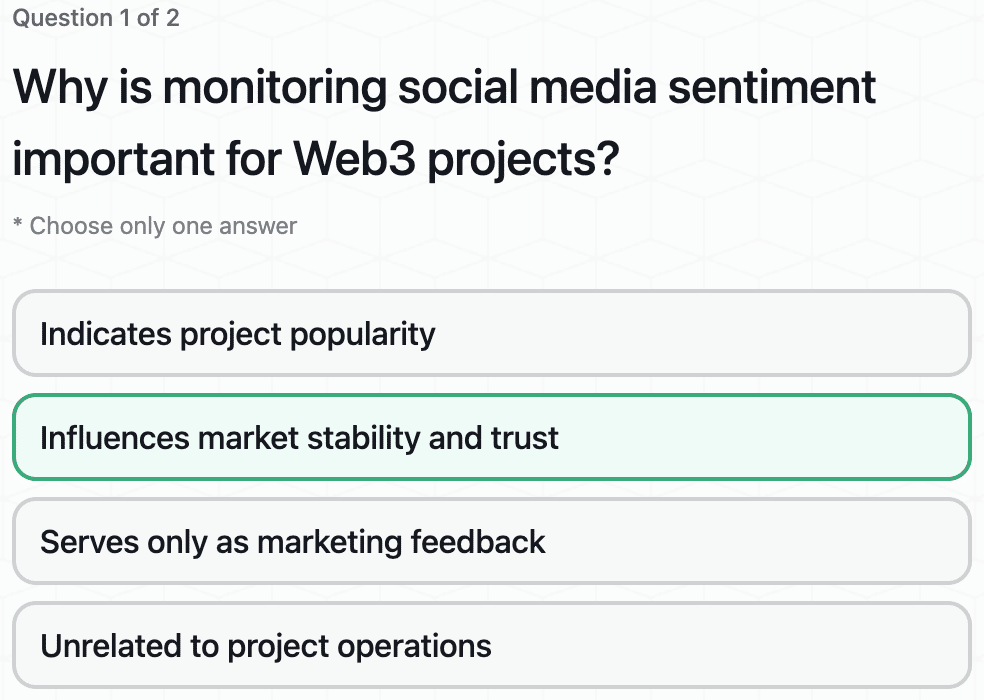


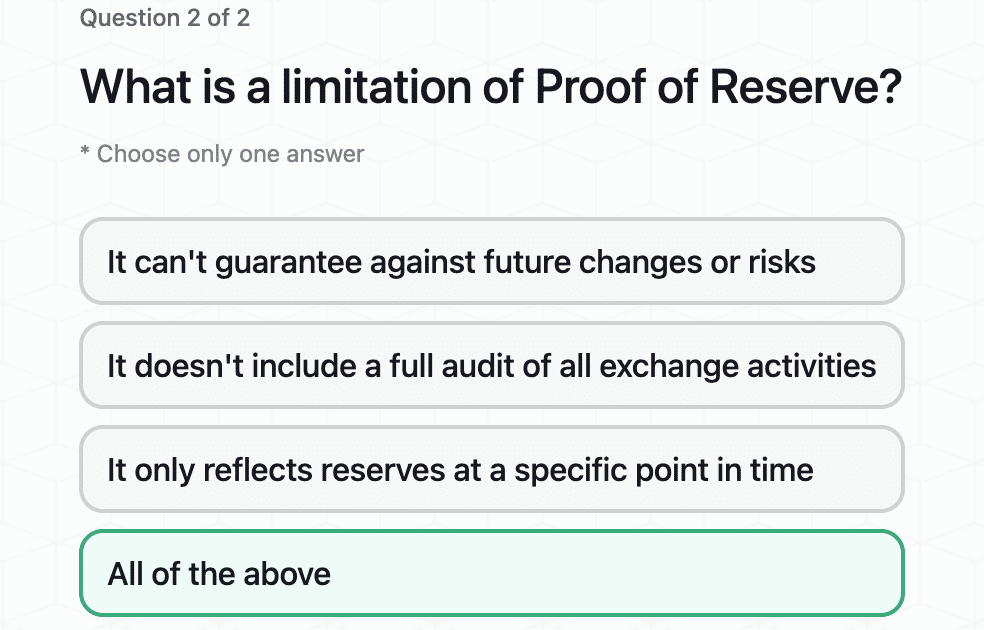
Important Exchange Security Features


Recognizing Risk Signals on the Exchange


Recognizing the Misuse of CertiK's Brand








Evaluating Security with Skynet Token Scan



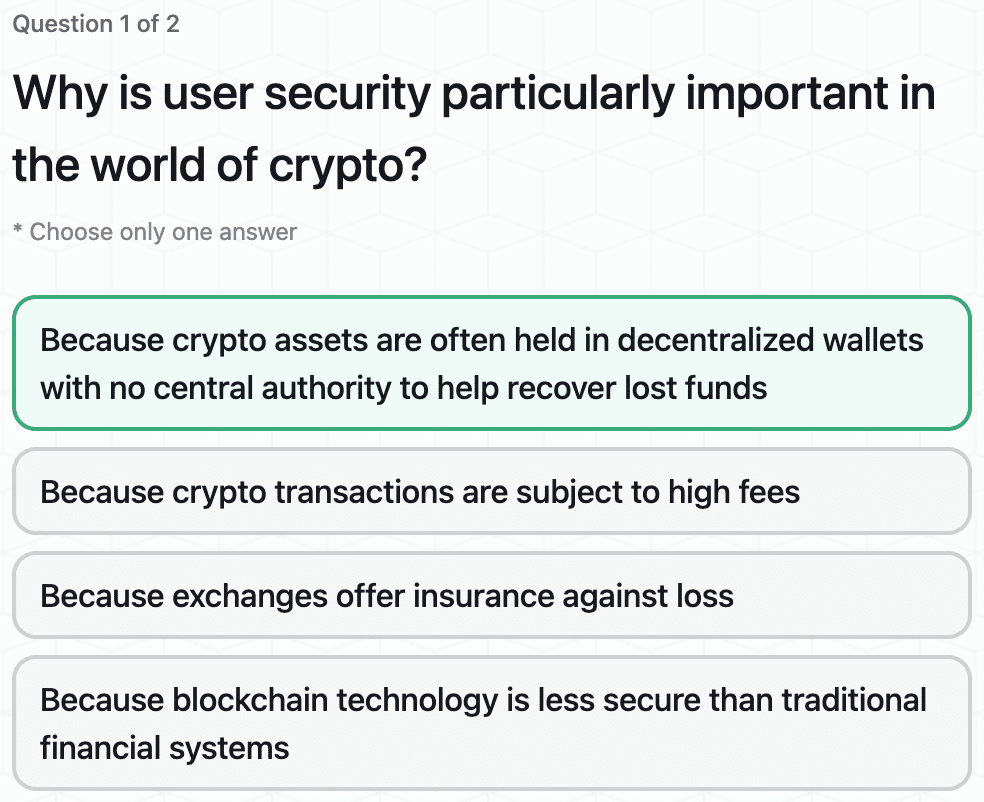
Introduction to Wallet Security
Question 1 of 2 : If the custodial service experiences a security breach, hack, or service itself becomes inaccessible, you may lose access to your private keys.
Question 2 of 2 : Storing them in a hardware wallet or encrypted offline location




Best Tools for Tracking Top Crypto Wallets



Question 1 of 2 : Predefined accounts for program execution
Question 2 of 2 : Use CPIs with trusted programs only
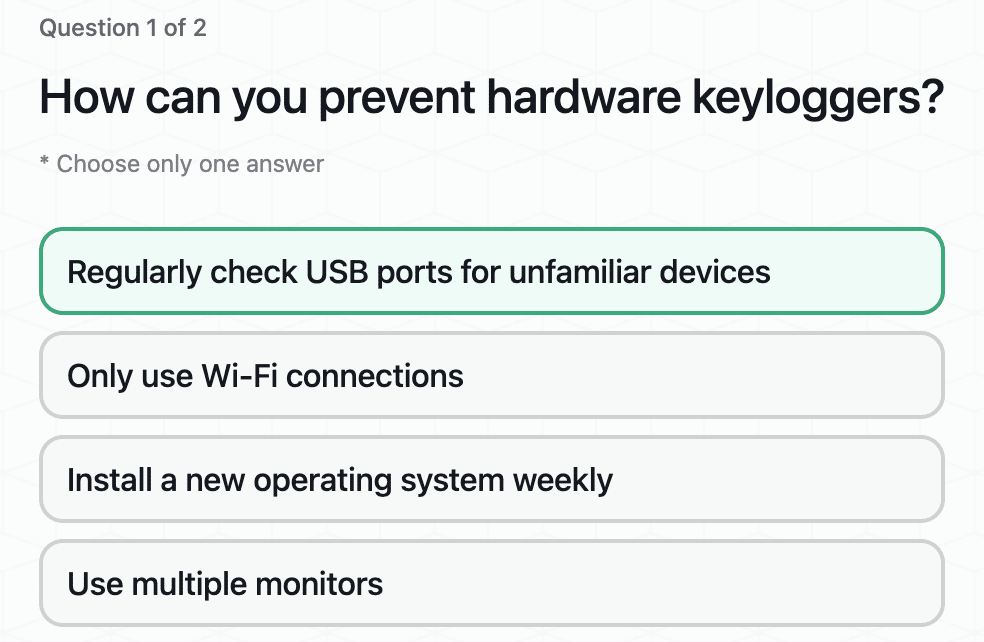
Private Key Security: Seed Phrases







