
CertiK Skynet Quest Answer (Industry Insights)
CertiK Skynetクエストの答えです。
当サイトに含まれる情報もしくは内容を利用することに伴い直接・間接的に生じた損失等に対し、当方は一切の責任を負いません。
ご自身の判断でご利用ください。
Industry Insights
Quantum Computing and the Future of Cryptocurrency Security


Blockchain Data Protection and Privacy Compliance


Unlocking Ethereum ETFs With BlackRock’s



Advanced Formal Verification of ZK Proofs
How AI is Transforming KYC for Crypto Project Teams

Understanding the Impact of FIT21 on Crypto Compliance


Understanding BGP Hijacking and Internet Routing Security



Unmasking Crypto Market Manipulation



AI Memecoins Explained: The New Craze in Crypto


Radiant Capital’s $50M DeFi Hack Response






How Binance Clawed Back $73M in Stolen Funds



Understanding AI's Role in Enhancing Web3 Security



Web2 Meets Web3: Hacking Decentralized Applications



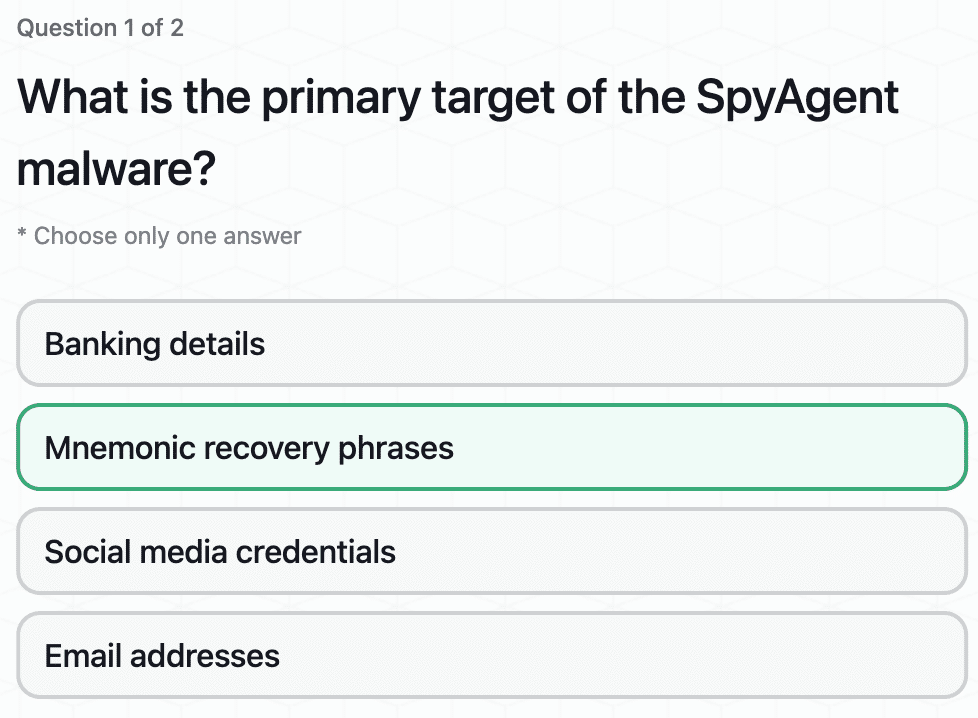
Understanding the Android SpyAgent Campaign

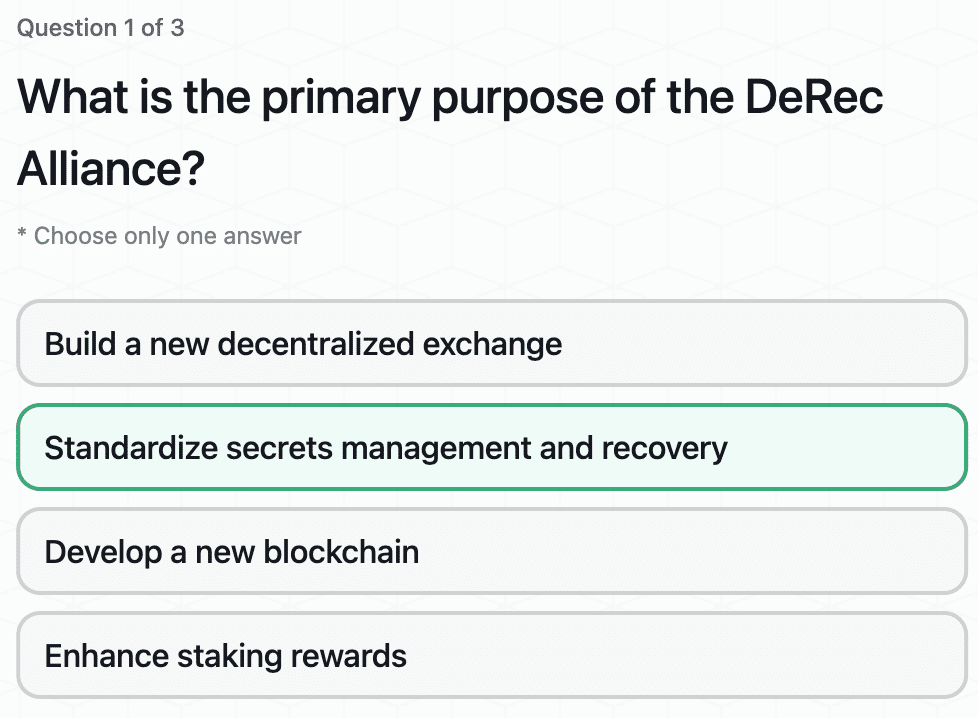
Understanding the DeRec Alliance


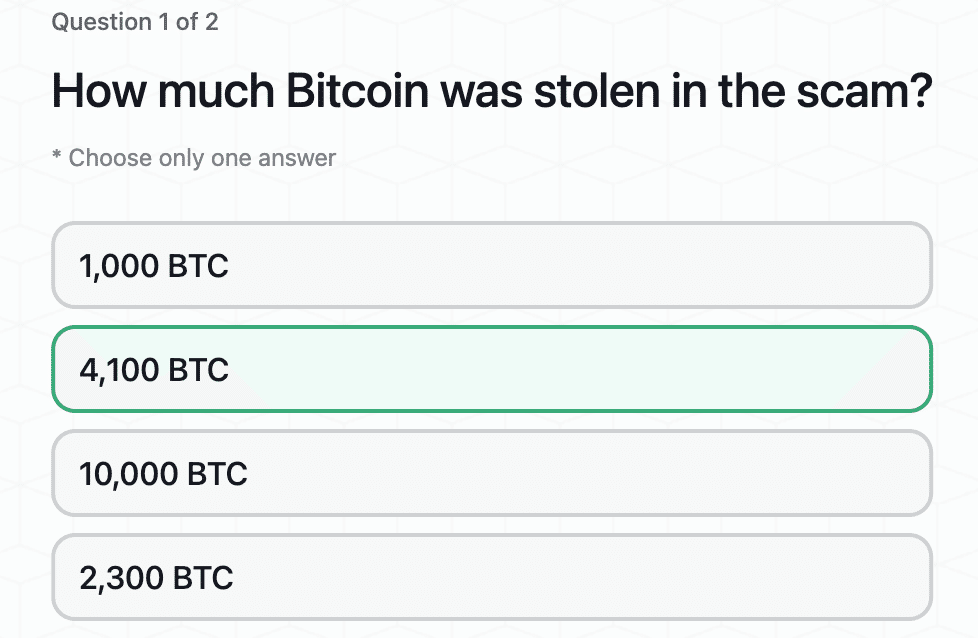
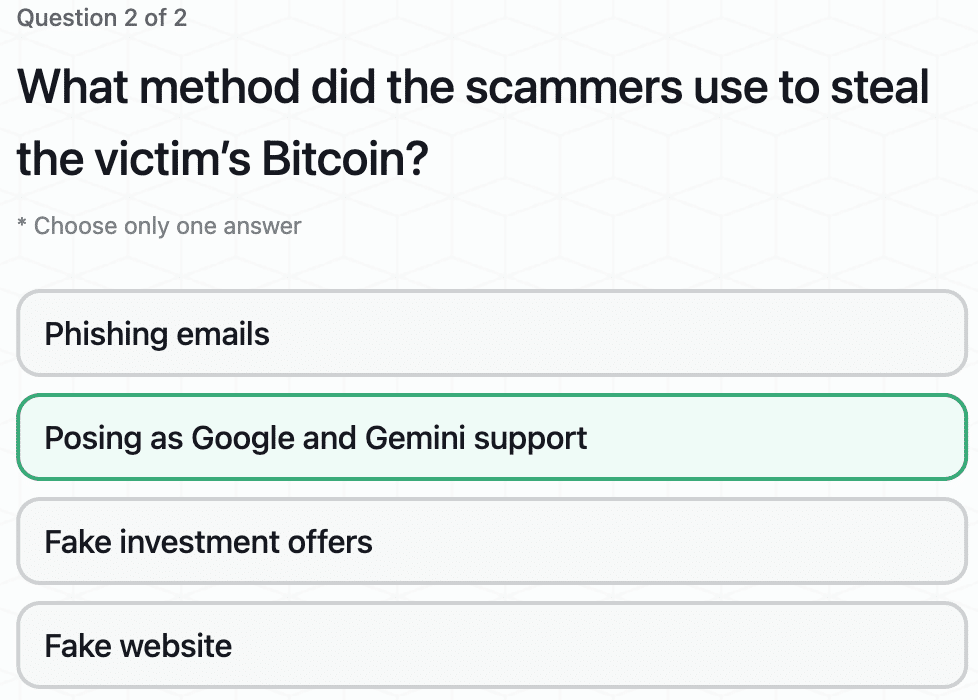
A $230M Bitcoin Scam Uncovered
How Exit Scammers Mint Tokens Undetected


Ordinals and the BRC-20 Standard


Top Performing Cryptocurrencies of H1 2024


Trap Phishing on Trusted Platforms

KYC Actors are Ramping Up Their Game


Build trust and integrity in project teams with KYC



Unveiling the KYC Actor Industry



Question 1 of 2 : False
Question 2 of 2: Small Teams
Bot-Driven Wash Trading in Exit Scams


FBI warns of Crypto Social Engineering


Vanity Address and Address Poisoning



Truth Terminal - An AI and a Crypto Millionaire







Understanding U.S. Crypto Tax Forms



Enhancing Security Awareness for Web3 Desktop Wallets
Navigating DAO Governance and the Compound DAO Incident





UtopiaSphere Incident Analysis


Hack3d Part 2: Major Hacks of Q3 2024


Hack3d Part 1: Most Common Attack Vectors in Q3 2024

HACK3D Part 3: Rounding Issue Exploits



HACK3D Part 2: Private Key Compromise



HACK3D Part 1: Top Incident Analyses


Hack3d Report Q2 H1 2024 - Part 2: Insights and Future Security Enhancements


Hack3d Report Q2 H1 2024 - Part 1: Overview and Key Highlights


SkyInsights: Crypto Compliance



OKX and CertiK Fast Pass Program
Question 1 of 2: Providing rigorous security audits for projects
Question 2 of 2: By receiving regular updates and detailed security reports
