HTB Help
ポート探索
nmap
$ nmap -sCV -A -v -Pn -p- --min-rate 5000 help.htb -oN nmap_result.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:bb:4d:9c:de:af:6b:bf:ba:8c:22:7a:d8:d7:43:28 (RSA)
| 256 d5:b0:10:50:74:86:a3:9f:c5:53:6f:3b:4a:24:61:19 (ECDSA)
|_ 256 e2:1b:88:d3:76:21:d4:1e:38:15:4a:81:11:b7:99:07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: HEAD POST OPTIONS
ポート80探索
$ nmap --script vuln -p 80 help.htb
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-15 19:12 JST
Nmap scan report for help.htb (10.10.10.121)
Host is up (0.46s latency).
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
|_ /support/: Potentially interesting folder
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
$ gobuster dir -u http://help.htb/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 100 -k -f
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://help.htb/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/javascript/ (Status: 403) [Size: 294]
/support/ (Status: 200) [Size: 4413]
/

/support

ソースコード
$ searchsploit helpdeskz
--------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------- ---------------------------------
HelpDeskZ 1.0.2 - Arbitrary File Upload | php/webapps/40300.py
HelpDeskZ < 1.0.2 - (Authenticated) SQL Injection / Unauthorized Fil | php/webapps/41200.py
Helpdeskz v2.0.2 - Stored XSS | php/webapps/52068.txt
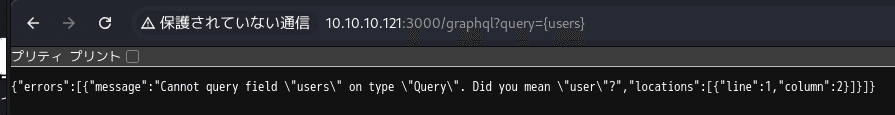
--------------------------------------------------------------------- ---------------------------------ポート3000探索
IPでnmapした時に3000もnode.jsのExpressがopenしていると出ていたので3000も確認




ExploitDB

HelpDeskZ 1.0.2 - Arbitrary File Upload
controllers/submit_ticket_controller.php line137-
・アップロードしたファイルは元のファイル名に現在時刻が付与されMD5でエンコードした結果をファイル名にしている
・/support/uploads/tickets/にファイルは保存される
・ファイル名のチェックをしてエラーメッセージを返しているがファイル自体は保存されたまま消されていない



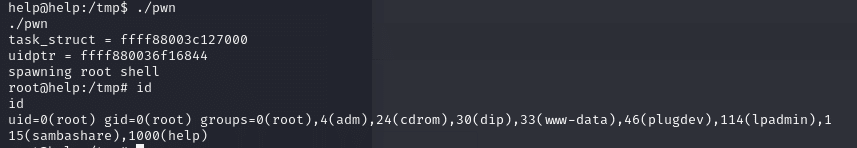
Privilege Escalation
name -a